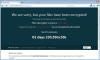
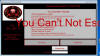
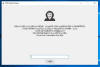
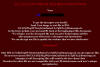
Ransom News
Datum
Název
Obrázek
Popis
30.3.19
New STOP Djvu Ransomware variants
![]()
Michael Gillespie found a new variants of the STOP Djvu Ransomware that append the .chech or .luceq extensions to encrypted files.
30.3.19
New .bk666 Dharma variant
![]()
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .bk666 extension to encrypted files.
30.3.19
Emsisoft has Released a Decryptor for the Hacked Ransomware
![]()
A decryptor for the Hacked Ransomware was released today by Emsisoft that allows victims to recover their files for free. This ransomware was active in 2017 and targeted English, Turkish, Spanish, and Italian users.
30.3.19
New STOP Djvu Ransomware variant
![]()
Michael Gillespie found new variants of the STOP Djvu Ransomware that append the .proden or .drume extensions to encrypted files.
30.3.19
New Matrix Ransomware variant
![]()
Michael Gillespie found new Matrix Ransomware variants that append the .MDEN or .SDEN extensions and drops a ransom note named !MDEN_INFO!.rtf or !SDEN_INFO!.rtf.
30.3.19
Ransomware hunt for YYYYBJQOQDU
![]()
Michael Gillespie is searching for a ransomware that appends the .YYYYBJQOQDU extension and drops a ransom note named YOUR FILES ARE ENCRYPTED.TXT.
30.3.19
New Paradise Ransomware variant
![]()
Michael Gillespie spotted a new Paradise Ransomware variant that appends the .securityP extension and drops a ransom note named Instructions with your files.txt.
30.3.19
STOPDecrypter Updated
Michael Gillespie updated the STOP decrypter with offline keys for .kroput1, .charck, .kropun, .doples, .luces, .luceq, .chech, .pulsar1, .drume, .tronas, .trosak, and .grovas, and .proden.
30.3.19
New BigBobRoss variant
![]()
Michael Gillespie found a new BigBobRoss Ransomware variant that uses the .encryptedALL and .djvu extensions.
30.3.19
New Xorist variant with long extension
Michael Gillespie found a Xoris Ransomware variant with the .NEED-TO-MAKE-PAYMENT-OR-ALL-YOUR-FILLES-WILL-BE-DELETED-CRITICAL-SITUATION-URGENT-ATTENTION-24-HOURS-TO-PAY-OR-EVERYTHING-WILL-BE-PERMANENTLY-DELETED-FOREVER. This ransomware is decryptable.
30.3.19
Another Xorist Variant
![]()
Michael found another Xorist variant that utilizes the extension ....VeraCrypt_System_Error2019-You_need_to_make_payment_in_maxmin_24_hours_if_you_dont_the_decryptor_license_will_be_deleted_this_is_not_a_joke.
30.3.19
Analysis of LockerGoga Ransomware
![]()
F-Secure posted a technical analysis of the LockerGoga ransomware:We recently observed a new ransomware variant (which our products detect as Trojan.TR/LockerGoga.qnfzd) circulating in the wild. In this post, we’ll provide some technical details of the new variant’s functionalities, as well as some Indicators of Compromise (IOCs).
30.3.19
UNNAM3D Ransomware Locks Files in Protected Archives, Demands Gift Cards
A new ransomware called Unnam3d R@nsomware is being distributed via email that will move a victim's files into password protected RAR archives. The ransomware then demands a $50 Amazon gift card code in order to get the archive password.
30.3.19
Ransomware Hits Garage of Canadian Domain Registration Authority
The parking garage used by employees of the Canadian Internet Registration Authority (CIRA) allowed people to park for free after computer systems were infected by ransomware.
30.3.19
New Rapid Ransomware variant
MalwareHunterTeam found a new Rapid Ransomware variant that uses the .GILLETTE extension and drops a ransom note named Decrypt DATA.txt.
30.3.19
New Stun Dharma Ransomware variant
![]()
Michael Gillespie found a new Dharma Ransomware variant that appends the .stun extension to encrypted files.
30.3.19
New STOP Djvu Ransomware variants
![]()
Michael found new variants of the STOP Djvu ransomware that append the .tronas, .trosak, and .grovas extensions to encrypted files.
30.3.19
New Swamp RAT Ransomware
![]()
Lawrence Abrams discovered a new RAT that pretends to be a ransomware called Swamp Rat. This is in-dev and quite bizarre.
30.3.19
New Scarab Ransomware variant
![]()
JAMESWT found a new Scarab Ransomware variant that appends the .crypt000 extension to encrypted files.
30.3.19
Avast updates their BigBobRoss Decryptor
![]()
Avast has updated their BigBobRoss decryptor to decrypt victims with the .encryptedALL variant.
30.3.19
Emsisoft updates their BigBobRoss Decryptor
![]()
Not to be outdone :), Emsisoft also updated their BigBobRoss decryptor to support the .encryptedAll variant.
30.3.19
New vxCrypter Ransomware
Lawrence Abrams discovered a new variant of the vxCrypter Ransomware that appends .xLck. This is in-development and deletes duplicate files on the computer.
24.3.19
New Snatch Ransomware variant
![]()
Michael Gillespie found a new variant of the Snatch Ransomware that appends the .jimm extension and drops a ransom note named Restore_JIMM_Files.txt.
24.3.19
Hated and hunted
![]()
Joe Tidy wrote an article about the life of ransomware expert Fabian Wosar:Fabian is world renowned for destroying ransomware - the viruses sent out by criminal gangs to extort money. Because of this, he lives a reclusive existence, always having to be one step ahead of the cyber criminals. He has moved to an unknown location since this interview was carried out.
24.3.19
ID Ransomware now tracks over 700 Ransomware families
![]()
Congrats to Michael Gillespie for setting up the terrific ID Ransomware service that now identifies 700 ransomware families.
24.3.19
Ransomware hunt for.L1LL Ransomware
![]()
Michael Gillespie is looking for a ransomware that appends the .L1LL extension to encrypted files.
24.3.19
New RotorCrypt Ransomware variant
![]()
Michael Gillespie has found a new RotorCrypt variant that appends the !!!! prusa@rape.lol !!!.prus extension and drops a ransom note named informprus.txt.
24.3.19
New GlobeImposter2 variant uses an interesting extension
![]()
Michael Gillespie found a new variant of the GlobeImposter 2.0 ransomware that adds the .{CALLMEGOAT@PROTONMAIL.COM}CMG extension to encrypted files.
24.3.19
Golden Axe Ransomware discovered
GrujaRS.discovered a new ransomware called Golden Axe that uses the .UIK1J extension for encrypted files. Unfortunately, it does not appear to be related to the classic Golden Axe video game :(
24.3.19
JNEC.a Ransomware Spread by WinRAR Ace Exploit
A new ransomware called JNEC.a spreads through an exploit for the recently reported code execution ACE vulnerability in WinRAR. After encrypting a computer, it will generate a Gmail address that victims need to create in order to receive the file decryption key once they pay the ransom.
24.3.19
New STOP Ransomware .charcl variant
![]()
Michael Gillespie found another STOP Djvu variant that appends the .charcl extension to encrypted files.
24.3.19
New Dharma variant
![]()
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .azero extension to encrypted files.
24.3.19
New FLKR Ransomware variant
![]()
Alex Svirid found a new variant of the FKLR Ransomware that appends the +jabber-winnipyh123@sj.ms extension to encrypted files.
24.3.19
LockerGoga Ransomware Sends Norsk Hydro Into Manual Mode
![]()
One of the largest aluminum producers in the world, Norsk Hydro, has been forced to switch to partial manual operations due to a cyber attack that is allegedly pushing LockerGoga ransomware.
24.3.19
LockerGoga variant uploaded from Norway
MalwareHunterTeam found a sample of the LockerGoga ransomware that was uploaded from Norway. Could this be the variant that affected Norsk Hydro?
24.3.19
Emsisoft releases decryptor for PewDiePie
![]()
Emsisoft has released a decryptor for the PewDiePie/PewCrypt Ransomware.
24.3.19
New variant of the Matrix Ransomware
Kshom found a new variant of the Matrix Ransomware that appends the [BIGBOSS777@airmail.cc].[random string].CRYPTO extension.
24.3.19
Donaldjtrumpware Ransomware is Yuuuuuge
MalwareHunterTeam found an old ransomware sample called donaldjtrumpware that was an in-development ransomware and did not save the decryption key.
24.3.19
Another LockerGoga variant
Because it's LockerGoga week, here is another variant found by GrujaRS.
24.3.19
Excellent analysis of LockerGoga
A thread by Lasha Khasaia offers excellent technical information on how LockerGoga works based on his reverse engineering of the sample.
24.3.19
Ransomware is not dead - a light analysis of LockerGoga
![]()
Another good technical article on LockerGoga byJoe Security.
24.3.19
New Xorist Variant
![]()
Michael Gillespie found a new Xorist Ransomware variant that appends the .Mr-X666 extension to encrypted files and drops a ransom note named HOW TO BACK YOUR FILES.txt.
24.3.19
New Doples STOP Djvu variant
![]()
Michael Gillespie found a new variant of the STOP Ransomware that appends the .doples extension to encrypted files.
24.3.19
New GarrantyDecrypt variant
![]()
Michael Gillespie found a new variant of the GarrantyDecrypt Ransomware that appends the .metan extension.
24.3.19
New hunt for Fox Ransomware
![]()
Michael Gillespie found a new ransomware that appends the id [numbers][Rabbit2002@pm.me].fox extension to encrypted files and drops a ransom note named Decrypt.txt.
24.3.19
New hunt for Robbin Hood Ransomware
Michael Gillespie found a new ransomware named Robbin Hood that appends the Encrypted_.enc_robbinhood extension and drops a ransom note named _Decryption_ReadMe.html.
24.3.19
Fake CDC Emails Warning of Flu Pandemic Push Ransomware
A new malspam campaign is being conducted that is pretending to be from the Centers for Disease Control and Prevention (CDC) about a new Flu pandemic. Attached to the emails are a malicious attachment that when opened will install the GandCrab v5.2 Ransomware on the target's computer.
24.3.19
Dharma ransomware recovery rates fall as ransom demands skyrocket
![]()
Coveware writes about "New Research on Dharma Ransomware: Data recovery rates decline as ransom demand skyrocket."
24.3.19
New STOP Djvu .Luces variant
![]()
Michael Gillespie found a new variant of the STOP Djvu ransomware that appends the .luces extension to encrypted files.
24.3.19
Rabbit Ransomware discovered
MalwareHunterTeam discovered the Rabbit Ransomware screenlocker. The unlock code is "RabbCompany66"
24.3.19
Police Federation in the UK have been hit with a ransomware attack
![]()
"We can confirm we have been subject to a malware attack on our computer systems. We were alerted by our own security systems on Saturday 9 March. Cyber experts rapidly reacted to isolate the malware and prevent it from spreading"
24.3.19
New Planetary Ransomware variant
GrujaRS found a new variant of the Planetary Ransomware that appends the .mira extension and drops a ransom note named !!!READ_IT!!!.txt.
24.3.19
Kaspersky think LockerGoga is affiliated with GrimSpider
![]()
Ivan Kwiatkowski has stated that his team at Kaspersky feels that LockerGoga is related to GrimSpider.
24.3.19
New GFS Scarab Ransomware variant
![]()
Michael Gillespie found a new Scarab Ransomware variant that appends the .[mrpeterson@cock.li].GFS extension to encrypted files.
24.3.19
New Suffer Scarab Ransomware variant
Amigo-A found a new variant of the Scarab Ransomware that appends the .suffer extension to encrypted files and creates ransom notes named HOW TO RECOVER ENCRYPTED FILES.TXT.
16.3.19
Ransomware Attack on Jackson County Gets Cybercriminals $400,000
![]()
A ransomware attack hit the computers of Jackson County, Georgia, reducing government activity to a crawl until officials decided to pay cybercriminals $400,000 in exchange for the file decryption key.
16.3.19
Emsisoft Decrypter for BigBobRoss
![]()
Emsisoft has released a decryptor for the BigBobRoss ransomware. It uses AES-128 ECB to encrypt files, and adds the extension ".obfuscated". Some variants also prepend the victim ID to the filename. The ransom note "Read Me.txt" asks the victim to contact "BigBobRoss@computer4u.com".
16.3.19
Avast releases a decryptor for BigBobRoss as well
![]()
Avast Threat Labs released a decryptor for BigBobRoss as well today.
16.3.19
New STOP Ransomware variant
![]()
Michael Gillespie found new variants of the STOP Ransomware that append the .promorad2 or .kroput extensions to encrypted files.
16.3.19
STOP Ransomware Installing Password Stealing Trojans on Victims
![]()
In addition to encrypting a victim's files, the STOP ransomware family has also started to install the Azorult password-stealing Trojan on victim's computer to steal account credentials, cryptocurrency wallets, desktop files, and more.
16.3.19
New Dharma variant
![]()
Jakub Kroustek found a new Dharma Ransomware variant that appends the .NWA extension to encrypted files.
16.3.19
Yatron Ransomware Plans to Spread Using EternalBlue NSA Exploits
A new Ransomware-as-a-Service called Yatron is being promoted on Twitter that plans on using the EternalBlue and DoublePulsar exploits to spread to other computer on a network. This ransomware will also attempt to delete encrypted files if a payment has not been made in 72 hours.
16.3.19
New bRcrypT Ransomware
![]()
Michael Gillespie found a new ransomware that appends the .bRcrypT extension and drops a ransom note named FILES ENCRYPTED.txt.
16.3.19
New RotorCrypt Ransomware
![]()
Michael Gillespie found a new RotorCrypt Ransomware variant that appends the !__help2decode@mail.com__.a800 extension and drops a ransom note named recovery.instruction.txt.
16.3.19
Updated STOPDecrypter
![]()
Michael Gillespie updated his STOPDecrypter to have more offline encryption keys. This one is for OFFLINE ID "0h7mFQcjRC3pDgsRcrWZ7K7bdAgvgDosJ24DmXt1" (.promorad2).
16.3.19
New GILLETTE Ransomware variant
![]()
Michael Gillespie found a new ransomware that appends the .GILLETTE extension and drops a ransom note named Decrypt DATA.txt.
16.3.19
New Matrix Ransomware variant
![]()
Michael Gillespie found a new Matrix ransomware that appends the .SCR extension to encrypted files.
16.3.19
New ransomware hunt
![]()
Michael Gillespie is search for a sample of the ransomware that appends the .yum extension and drops a ransom note named !!!READ_IT!!!.txt.
16.3.19
New Dharma Ransomware variant
![]()
Jakub Kroustek found a new Dharma Ransomware variant that appends the .com extension to encrypted files.
16.3.19
Updated STOPDecrypter
![]()
Michael Gillespie updated his STOPDecrypter to have more offline encryption keys. This one is for OFFLINE ID "upOacGl1yOz9XbrhjX9UR2M0j8i03YwVB0pXr1t1" (.kroput).
16.3.19
New Scarab variant pretends to be GandCrab
![]()
Amigo-A found a new variant of the Scarab Ransomware that pretends to be GandCrab by using the .[crab2727@gmx.de].gdcb and dropping a ransom note named GDCB-DECRYPT.TXT.
16.3.19
MegaLocker Virus discovered
MalwareHunterTeam found a new ransomware called MegaLocker Virus that appends the .crypted extension to encrypted files and drops a ransom note named !DECRYPT INSTRUCTION.TXT. Appears to have encrypted a web server in the image.
16.3.19
New 0kilobypt Ransomware variant
![]()
Amigo-A discovered a new variant of the 0kilobypt Ransomware that appends the .crypt extension to encrypted files.
16.3.19
New STOP Ransomware variants
![]()
Michael Gillespie found new STOP ransomware variants that append the .kroput1, .pulsar1 or .charck extensions to encrypted files.
16.3.19
New Ransomware hunt for Scorpion Ransomware
Michael Gillespie is looking for a new ransomware that appends the .Scorpion extension and drops a ransom note named About .Scorpion V4.0 unlocking instructions.txt.
16.3.19
New Ransomware hunt
![]()
Michael Gillespie is looking for a new ransomware that appends the .[w_decrypt24@qq.com].zq extension.
16.3.19
New Paradise Ransomware variant
![]()
Michael Gillespie found a new Paradise Ransomware variant that appends the _[id]_{babyfromparadise666@gmail.com}.p3rf0rm4 and drops a ransom note named Instructions with your files.txt.
16.3.19
New Jamper Ransomware
![]()
Michael Gillespie is looking for a new ransomware that appends the .jamper extension and drops a ransom note named ---README---.TXT.
16.3.19
New RotorCrypt variant
![]()
Michael Gillespie found a new RotorCrypt variant that appends the !@#$%^&-().1c and drops a ransom note named INFO.txt.
16.3.19
New STOP Ransomware variants
![]()
Michael Gillespie found new STOP Ransomware variants that append the .kropun or .klope extensions to encrypted file's names.
9.3.19
Ransomware Pretends to Be Proton Security Team Securing Data From Hackers
A recent variant of the GarrantyDecrypt ransomware has been found that pretends to be from the security team for Proton Technologies, the company behind ProtonMail and ProtonVPN.
9.3.19
CrazyCrypt 4.1 discovered
MalwareHunterTeam found the new 4.1 variant of CrazyCrypt 4.1 that drops a ransom note named FILES ENCRYPTED.txt.
9.3.19
New Korea Dharma variant
![]()
Jakub Kroustek found a new Dharma Ransomware variant that uses the .korea extension.
9.3.19
#OpJerusalem Targeted Israeli Windows Users with JCry Ransomware
Over the weekend, hundreds of popular Israeli sites were targeted by an attack called #OpJerusalem whose goal was to infect Windows users with the JCry ransomware. Thankfully, a mistake in the attacker's code caused the page to show a defacement rather than causing the ransomware to be distributed.
9.3.19
Annabelle 2.1 becomes a wiper
Michael Gillespie found a new variant of the Annabelle Ransomware that has become a wiper due to shoddy coding.
9.3.19
New GlobeImposter 2.0 variant
![]()
Michael Gillespie found a new GlobeImposter 2.0 Ransomware variant that appends the .{mattpear@protonmail.com}MTP extension.
9.3.19
Neptune Ransomware
![]()
Michael Gillespie found a new ransomware that appends the .Neptune extension. This family has been releasing variants utilizing extensions named after planets.
9.3.19
New ransomware hunt
![]()
Michael Gillespie is looking for a ransomware that appends the .[help24decrypt@cock.li and drops a ransom note named How to decrypt.txt.
9.3.19
New Satan Ransomware variant
![]()
Michael Gillespie found a new variant of the Satan/Lucky that uses the .evopro extension and drops a ransom note named _如何解密我的文件_.txt. According xiaopao, this is a Satan variant.
9.3.19
New Seed Locker Everbe Ransomware variant
MalwareHunterTeam found a new variant of the Everbe 2.0 ransomware called Seed Locker. This infection will append the .seed extension to encrypted files and drops a ransom note named !#_How_to_decrypt_files_$!.txt.
9.3.19
CryptoMix Clop Ransomware Says It's Targeting Networks, Not Computers
A new CryptoMix Ransomware variant has been discovered that appends the .CLOP or .CIOP extension to encrypted files. Of particular interest, is that this variant is now indicating that the attackers are targeting entire networks rather than individual computers.
9.3.19
Jokeroo Ransomware-as-a-Service Offers Multiple Membership Packages
A new Ransomware-as-a-Service called Jokeroo is being promoted on underground hacking sites and via Twitter that allows affiliates to allegedly gain access to a fully functional ransomware and payment server.
9.3.19
New Scarab Ransomware variant
Emmanuel_ADC-Soft found a new Scarab Ransomware variant that appends the .kitty extension to encrypted files and drops a ransom note named HOW-TO-RESTORE-FILES.txt.
9.3.19
New ICP Ransomware
![]()
Michael Gillespie is looking for a new ransomware that appends the .icp extension to encrypted files and drops a ransom note named Restore_ICPICP_Files.txt.
9.3.19
New .plomb Dharma variant
![]()
Michael Gillespie found a new Dharma variant that appends the .id-[id].[plombiren@hotmail.com].plomb extension.
9.3.19
New Scarab Ransomware variant
GrujaRS found a new Scarab Ransomware variant that appends the .dy8wud and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
9.3.19
New W1F1RANSOM screenlocker discovered
![]()
MalwareHunterTeam found a new screenlocker called W1F1RANSOM or W1F1SN1FF3R that uses an unlock key of 0000.
9.3.19
StopDecrypter Updated
Michael Gillespie added more OFFLINE keys to his StopDecrypter program. These are for the .promoz, .promok, .promorad, .promok variants.
2.3.19
GarrantyDecrypt Ransomware
![]()
Michael Gillespie found a new ransomware called GarrantyDecrypt that appends the .cammora extension.
2.3.19
New DeltaSEC Jigsaw Ransomware
MalwareHunterTeam found a new Jigsaw Ransomware variant called DeltaSEC.
2.3.19
New Russian ransomware variant
Michael Gillespie found a new ransomware that appends the .infileshop@gmail_com_ID44 and drops a ransom note named ! ПРОЧТИ МЕНЯ !.html.
2.3.19
New Scarab Ransomware variant
Emmanuel_ADC-Soft found a new variant of the Scarab Ransomware that appends the .X3 extension and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
2.3.19
GandCrab Decrypter Available for v5.1, New 5.2 Variant Already Out
A free file decryption tool is available for users whose computers got infected with the latest confirmed versions of GandCrab. It can unlock data encrypted by versions 4 through 5.1 of the malware, and some earlier releases of the threat.
2.3.19
New Ransomware pretends to be from ProtonMail
Michael Gillespie found a new ransomware that drops a ransom note named SECURITY-ISSUE-INFO.txt and pretends to be from the security team at ProtonMail.
2.3.19
New Promos STOP variant
![]()
Michael Gillespie found a new variant of the STOP/DJVU Ransomware that appends the .promos extension to encrypted files.
2.3.19
New Seed Locker Ransomware
Emmanuel_ADC-Soft found a new ransomware that appends the .seed extension and drops a ransom note named !#_How_to_decrypt_files_#!.
2.3.19
Formjacking Surpasses Ransomware and Cryptojacking as Top Threat of 2018
![]()
A new year in review report from Symantec shows that formjacking accompanied by supply chain attacks were the fastest growing threats of 2018, while living-off-the-land (LotL) attacks saw a large boost in adoption from threat actors, with PowerShell scripts usage, for example, seeing a formidable 1000% increase.
2.3.19
Cekisan Ransomware discovered
![]()
Michael Gillespie found a new ransomware that appends the .cekisan extension and drops a ransom note named Readme_Restore_Files.txt.
2.3.19
New Aqva Dharma variant
![]()
Jakub Kroustek found a new Dharma Ransomware variant that appends the .aqva extension to encrypted files.
2.3.19
GandCrab Ransomware Affiliates Continue to Push Decryptable Versions
![]()
GandCrab Ransomware affiliates are doing their victims a favor by screwing up and distributing a version of the ransomware that can be decrypted for free.
2.3.19
New BlackPink Ransomware
![]()
Michael Gillespie saw a new ransomware uploaded to ID Ransomware that appends the .BlackPink extension to encrypted files and has a Korean ransom note named how_to_recver_files.txt.
2.3.19
New Russian Ransomware
![]()
Michael Gillespie found a new Russian ransomware that drops a ransom note named инструкция по оплате.txt.
2.3.19
New Ransomware appends .crazy
![]()
Michael Gillespie found a new ransomware that appends the .id.[id].[[emai]].crazy extension to encrypted files and drops a ransom note named FILES ENCRYPTED.txt.
2.3.19
New Matrix Ransomware variant
![]()
Michael Gillespie is on fire with a new Matrix Ransomware variant that appends the .GBLOCK extension and drops a ransom note named !GBLOCK_INFO.rtf.
2.3.19
Cr1ptT0r Ransomware Infects D-Link NAS Devices, Targets Embedded Systems
A new ransomware called Cr1ptT0r built for embedded systems targets network attached storage (NAS) equipment exposed to the internet to encrypt data available on it.
2.3.19
New .AYE Dharma variant
![]()
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .AYE extension to encrypted files.
2.3.19
Ransomware Dogge discovered
Dodge This Security found a new ransomware called Dogge Ransomware. Appears to be a joke ransomware.
2.3.19
B0r0nt0K Ransomware Wants $75,000 Ransom, Infects Linux Servers
A new ransomware called B0r0nt0K is encrypting victim's web sites and demanding a 20 bitcoin, or approximately $75,000, ransom. This ransomware is known to infect Linux servers, but may also be able to encrypt users running Windows.
2.3.19
New Xorist Ransomware variant
GrujaRS found a Xorist Ransomware sample that appends only a period as an extension and drops a ransom note named HOW TO DECRYPT FILES.txt.
2.3.19
D-Link advisory on Cr1ptT0r
![]()
D-Link issued a security advisory on the Cr1ptT0r Ransomware.
2.3.19
CrazyCrypt Ransomware discovered
MalwareHunterTeam found a new Stupid Ransomware variant called CrazyCrypt 2.1.
2.3.19
New Artemy Scarab Ransomware variant
GrujaRS found a new Scarab Ransomware variant that appends the .ARTEMY extension to encrypted files.
2.3.19
New Phobos Ransomware variant
Jakub Kroustek found a new Phobos Ransomware variant that appends the .Frendi extension.
2.3.19
New Matrix Ransomware variant
![]()
Michael Gillespie found a new Matrix Ransomware variant that appends the .SBLOCK extension and drops a ransom note named !SBLOCK_INFO!.rtf.
2.3.19
New STOP/DJVU Variant
![]()
Michael Gillespie found a new STOP/DJVU variant that appends the .promoz.
2.3.19
Florida ISP's service impacted by ransomware
![]()
The Tallahassee Democrat reports: A ransomware attack targeting Network Tallahassee kept customers from getting online, sending or receiving emails or accessing website domains, which were completely shutdown.
2.3.19
New RotorCrypt Sample
![]()
Michael Gillespie found a new RotorCrypt sample that appends the !_!email__ prusa@goat.si __!..PAYMAN extension and drops a ransom note named open_payman.txt.
2.3.19
CSP Ransomware
![]()
Michael Gillespie is looking for a new ransomware variant that appends the _csp extension and drops a ransom note named HOW TO DECRYPT[1T0tO].txt.
2.3.19
New STOP/DJVU variants
![]()
Michael Gillespie found a new variant of the STOP/DJVU Ransomware that appends the .promorad and .promock.
16.2.19
New FCRYPT Ransomware
GrujaRS found a new ransomware called FCRYPT that appends the .FCrypt extension and drops a ransom note named #HELP-DECRYPT-FCRYPT1.1#.txt to encrypted files. Michael Gillespie stated it can be decrypted.
16.2.19
New Matrix Ransomware variant
![]()
Michael Gillespie found a new Matrix Ransomware variant that appends the .PLANT extension to encrypted files.
16.2.19
New Ransomware has trouble spelling planets
![]()
Michael Gillespie found a new ransomware variant that tried to spell "Mercury", but used .mecury as the extension for encrypted files.
16.2.19
Ransomware Story Comic
![]()
Christiaan Beek and Hackerstrip teamed up to create a comic about ransomware.
16.2.19
New Encrypted5 ransomware
GrujaRS found a new ransomware variant that appends the .Encrypted5.
16.2.19
New Matrix Ransomware variant
![]()
Michael Gillespie found a new variant of the Matrix Ransomware that appends the .PEDANT and drops a ransom note named !PEDANT_INFO!.rtf.
16.2.19
Ransomware Attacks Target MSPs to Mass-Infect Customers
![]()
Ransomware distributors have started to target managed service providers (MSPs) in order to mass-infect all of their clients in a single attack. Recent reports indicate that multiple MSPs have been hacked recently, which has led to hundreds, if not thousands, of clients being infected with the GandCrab Ransomware.
16.2.19
New Dharma variant
![]()
Jakub Kroustek found a new variant of the Dharma ransomware that appends the .KARLS extension to encrypted files.
16.2.19
New Snatch Ransomware variant
GrujaRS found a new Snatch ransomware variant appends the .jupstb extension to encrypted files.
9.2.19
New PayDay Ransomware variant
MalwareHunterTeam found a new variant of the PayDay Ransomware that uses a ransom note named HOW_TO_DECRYPT_MY_FILES.txt.
9.2.19
New variant of the STOP Ransomware
![]()
dis found a new variant of the STOP Ransomware that uses the .blower extension.
9.2.19
New RotorCrypt variant
![]()
Michael Gillespie found a new variant of the RotorCrypt Ransomware that appends the "!ymayka-email@yahoo.com.cryptotes" extension.
9.2.19
New Dharma variant
![]()
Michael Gillespie found a new variant of the Dharma Ransomware that appends the .888 extension.
9.2.19
New PennyWise Jigsaw Ransomware variant
MalwareHunterTeam found a new Jigsaw Ransomware that uses the .PennyWise extension for encrypted files.
9.2.19
Crypted Pony Ransomware found
![]()
Petrovic found a new ransomware that appends the .crypted_pony_test_build_xxx_xxx_xxx_xxx_xxx extension to encrypted files.
9.2.19
Cryptojacking Overtakes Ransomware, Malware-as-a-Service on the Rise
![]()
Cryptominers infected roughly ten times more organizations during 2018 than ransomware did, however only one in five security professionals knew that their company's systems have been impacted by a malware attack as reported by Check Point Research.
9.2.19
GandCrab Ransomware Helps Shady Data Recovery Firms Hide Ransom Costs
![]()
The GandCrab ransomware TOR site allows shady data recovery companies to hide the actual ransom cost from victims and it is currently being disseminated through a large assortment of distribution channels according to a Coveware report.
9.2.19
Russian ransomware with a valid cert
MalwareHunterTeam found a Russian ransomware sample that drops a ransom note named Your files are now encrypted.txt but does not use an extension. Uses a valid certificate.
9.2.19
New Ransomware appends FileSlack
![]()
Michael Gillespie found a new Ransomware that appends the .FileSlack extension and drops a ransom note named Readme_Restore_Files.txt.
9.2.19
Looking for a sample of Pluto Ransomware
![]()
Michael Gillespie is looking for a ransomware sample that appends the .pluto extension and drops a ransom note named !!!READ_IT!!!.txt.
9.2.19
LOLSEC Jigsaw Ransomware variant
Michael Gillespie found a new Jigsaw Ransomware variant that appends .paycoin to encrypted files and uses the following background.
9.2.19
New Dharma variant found
![]()
Jakub Kroustek found new Dharma variants that appends the .amber or .frend extension.
9.2.19
Mail Attachment Builds Ransomware Downloader from Super Mario Image
![]()
A malicious spreadsheet has been discovered that builds a PowerShell command from individual pixels in a downloaded image of Mario from Super Mario Bros. When executed, this command will download and install malware such as the GandCrab Ransomware and other malware.
9.2.19
New Clop Ransomware
![]()
Michael Gillespie found a new ransomware that appends the .Clop extension to encrypted file names and drops a ransom note named ClopReadMe.txt.
9.2.19
Gandcrab via fake invoice using password protected zip files
![]()
My Online Security reports: It’s Friday afternoon at the end of a busy week for many people and we get yet another Gandcrab ransomware campaign. This campaign is slightly different to previous versions that I have seen. We generally see Gandcrab delivered via Office ( normally Word) documents, either Macros or possibly Equation editor or other embedded ole object exploits. Today’s version is the first time that I have seen a js file inside a zip that was password protected as the initial vector. You need the password “invoice123” to be able to open the zip file.
2.2.19
New Scarab Ransomware variant
![]()
Amgad.M found a new Scarab Ransomware variant that appends the .Crash extension to encrypted files.
2.2.19
Akron says cyberattack forced shutdown of city help line
![]()
WHIO-TV reports: Officials say a financially motivated cyberattack on computer servers forced an Ohio city to shut down its 311 call center line as it prepared to dig out from a snowstorm. The Akron Beacon Journal reports a city of Akron spokeswoman says the attack included ransomware that demanded thousands of dollars. Ransomware is malicious software that threatens to publish a target's data or block access to it.
2.2.19
New Xorist Ransomware
![]()
Petrovic discovered a new Xorist variant that appends the .mcafee extension to encrypted files.
2.2.19
Blackware Ransomware discovered
MalwareHunterTeam discovered the Blackware Ransomware 1.0 that is only a screenlocker. Does not encrypt.
2.2.19
Spiteful Doubletake Ransomware discovered
Jakub Kroustek has discovered a ransomware written in Perl called Spiteful Doubletake that appears to be in-development or a PoC. Appends the .enc extension to encrypted files.
2.2.19
New STOP .adobee variant
![]()
Michael Gillespie found a new STOP Ransomware variant that appends the .adobee extension to encrypted files.
2.2.19
Gorgon Ransomware discovered
Jakub Kroustek discovered the Gorgon Ransomware that appends the .[buy-decryptor@pm.me] extnesion to encrypted files.
2.2.19
Russia hit by new wave of ransomware spam
![]()
January 2019 has seen a dramatic uptick in detections of malicious JavaScript email attachments, an attack vector that mostly lay dormant throughout 2018. Among the “New Year edition” of malicious spam campaigns relying on this vector, we have detected a new wave of Russian-language spam that distributes ransomware known as Shade or Troldesh, and detected by ESET as Win32/Filecoder.Shade.
2.2.19
Unit09 Ransomware discovered
![]()
Michael Gillespie found a new ransomware that appends the .UNIT09 extension to encrypted files and drops a ransom note named $!READ ME.txt.
2.2.19
New .mbrcodes Xorist variant found
![]()
Michael Gillespie found a new Xoris Ransomware variant that appends the .mbrcodes extension.
2.2.19
Anti-Capitalist Jigsaw Ransomware variant found
MalwareHunterTeam found a new Jigsaw Ransomware variant called Anti-Capitalist that appends the .fun extension to encrypted files.
2.2.19
DESYNC Ransomware Discovered
![]()
Michael Gillespie found a new ransomware that appends the .DESYNC extension to encrypted files and drops a ransom note named # HOW TO DECRYPT YOUR FILES #.txt.
2.2.19
Love Letter Malspam Serves Cocktail of Malware, Heavily Targets Japan
![]()
The "Love Letter" malspam campaign which was previously detected and analyzed on January 10, has now changed its focus to Japanese targets and almost doubled the volume of malicious attachments it delivers, including GandCrab.
2.2.19
New LockerGoga Ransomware Allegedly Used in Altran Attack
![]()
Hackers have infected the systems of Altran Technologies with malware that spread through the company network, affecting operations in some European countries. To protect client data and their own assets, Altran decided to shut down its network and applications.
2.2.19
Xorist Ransomware variant
GrujaRS found a new Xorist variant that appends the .Mcafee extension and drops a ransom note named HOW TO DECRYPT FILES.
2.2.19
Looking Into Jaff Ransomware
Jaff ransomware was originally released in the spring of 2017, but it was largely neglected because that was the same time that WannaCry was the lead story for news agencies around the world. Since that time, Jaff ransomware has lurked in the shadows while infecting machines worldwide. In this FortiGuard Labs analysis, we will look into some of the common ransomware techniques used by this malware, and how it represents the ransomware’s infection routine in general.
2.2.19
Flurry of Dharma variant discovered
![]()
Jakub Kroustek found a few new Dharma variants that append the .qwex, .ETH, or .air extension to encrypted files.
2.2.19
New Obfuscated Ransomware variant
![]()
Michael Gillespie found a new variant of the Obfuscated Ransomware that prepends "[id=]" to encrypted files. Still decryptable.
2.2.19
Jigsaw variant discovered
Michael Gillespie found a Jigsaw Ransomware variant that appends the .YOLO extension to encrypted files. Possible Red Team/Blue Team exercise based on ransom message?
2.2.19
Matrix: A Low-Key Targeted Ransomware
![]()
Sophos security research Luca Nagy released an research paper on the Matrix Ransomware.
27.1.19
New AUF Dharma variant
![]()
Jakub Kroustek discovered a new Dharma Ransomware variant that appends the .AUF extension to encrypted files.
27.1.19
Ransomware Attacks May Soon Require Disclosure in North Carolina
![]()
North Carolina’s Attorney General Josh Stein and Rep. Jason Saine proposed legislation designed to strengthen the state's identity theft protection law, targeting prevention and consumer protection boost in the face of breaches.
27.1.19
New Rumba STOP Ransomware Being Installed by Software Cracks
The STOP ransomware has seen very heavy distribution over the last month using adware installers disguised as cracks. This campaign continues with a new variant released over the past few days that appends the .rumba extension to the names of encrypted files. Michael Gillespie also reported finding a variant utilizing the .shadow extension.
27.1.19
STOP Ransomware decryptor updated for offline DJVU variants
Michael Gillespie updated his STOP Decryptor to decrypt the offline versions of the DJVU variants.
27.1.19
New Dharma variants discovered
![]()
Jakub Kroustek discovered two more Dharma variants that utilize the .USA, .xwx, and .best extensions for encrypted files.
27.1.19
New variant of Ryuk using project name of Cryptor 2.0
![]()
MalwareHunterTeam found a new Ryuk variant that uses an internal project name of "Cryptor 2.0".
27.1.19
New Matrix Ransomware variant
![]()
Michael Gillespie found a new variant of the Matrix Ransomware that appends the .GMBN extension and drops a ransom note named !README_GMBN!.rtf. Michael found another variant that uses the .SPCT extension.
27.1.19
New .heets Dharma variant
![]()
Coveware found a new Dharma variant that is appending the .heets extension to encrypted files.
27.1.19
New Anatova Ransomware Supports Modules for Extra Functionality
A new ransomware family called Anatova has popped on the radar of analysts, who see it as a serious threat created by skilled authors that can turn it into a multifunctional piece of malware.
27.1.19
STOP Ransomware variant uses .adobe
![]()
Michael Gillespie found a new variant of the STOP Ransomware that utilizes the .adobe variant. This extension was previously used by the Dharma ransomware.
27.1.19
New BSS Hidden Tear variant
![]()
MalwareHunterTeam found someone named Dennis playing with a Hidden Tear variant named "Ransomware by BSS".
27.1.19
New ransomware strain is locking up Bitcoin mining rigs in China
![]()
A new strain of ransomware has been observed targeting Bitcoin mining rigs. At the time of writing, most of the infections have been reported in China, the country where most of the world's cryptocurrency mining farms are located.
27.1.19
New JSWorm Ransomware
MalwareHunterTeam found the JSWorm Ransomware that appends the .JSWORM extension and drops a ransom note named JSWORM-DECRYPT.html.
27.1.19
Beware of Exit Map Spam Pushing GandCrab v5.1 Ransomware
![]()
A new malspam campaign pretending to be the current emergency exit map for the recipient's building is being used to install the GandCrab Ransomware. These spam emails contain malicious Word documents that download and install the infection from a remote computer.
27.1.19
New Xorist variant
![]()
Petrovic found a new Xorist variant that appends the .vaca etension to encrypted files.
27.1.19
New Cyspt ransomware
MalwareHunterTeam found the Cyspt ransomware that appends the .OOFNIK extension to encrypted files.
27.1.19
New Scarab Ransomware variant
found a new Scarab Ransomware variant that appends the .GEFEST extension and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
27.1.19
GandCrab is not a RaaS
Damian has stated that according to a post at Exploit.in, the developers behind GandCrab have denied being part of a RaaS.
27.1.19
New ransomware variant
A new unknown ransomware was discovered by lc4m that appends the .locked extension and drops a ransom note named README-NOW.txt.
19.1.19
New Krab Scarab Ransomware variant
Amigo-A found a new variant of of the Scarab Ransomware that appends the .Krab extension to encrypted files and drops a ransom note named !!! RETURN YOUR FILES !!!.TXT.
19.1.19
New .zzzzzzzz Scarab Ransomware variant
Emmanuel_ADC-Soft found a new sleepy variant of the Scarab Ransomware that appends the .zzzzzzzz extension to encrypted files and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
19.1.19
New PPAM GlobeImposter 2 variant
![]()
Petrovic found a new variant of the GlobeImposter2 that appends the .ppam extension to encrypted file names.
19.1.19
New ransomware appends mdk4y
Leo found a new ransomware that appends the .mdk4y extension to encrypted file names.
19.1.19
New French Jigsaw Ransomware variant
![]()
Michael Gillespie found a new French Jigsaw Ransomware variant that appends the .data extension.
19.1.19
New Matrix Ransomware variant
![]()
Michael Gillespie found a new Matrix Ransomware variant that appends the .GRHAN extension and drops a ransom note named !README_GRHAN!.rtf.
19.1.19
New TrumpHead Ransomware
MalwareHunterTeam found a new ransomware called TrumpHead that contains text that sounds like, well, Trump.
19.1.19
Djvu Ransomware Spreading New .TRO Variant Through Cracks & Adware Bundles
In December 2018, a new ransomware called Djvu, which could be a variant of STOP, was released that has been heavily promoted through crack downloads and adware bundles. Originally, this ransomware would append a variation of the .djvu string as an extension to encrypted files, but a recent variant has switched to the .tro extension.
19.1.19
New Ransomware Bundles PayPal Phishing Into Its Ransom Note
A new in-development ransomware has been discovered that not only encrypts your files, but also tries to steal your credit card information with an included PayPal phishing page.
19.1.19
New IsraBye is repeating itself
MalwareHunterTeam found a new IsraByte variant that seems to be repeating itself with the extension.
19.1.19
New Paradise Ransomware variant
![]()
MalwareHunterTeam found a new Paradise ransomware variant that drops a ransom note named Instructions with your files.txt and uses the extension _%ID%_{admin@prt-decrypt.xyz}.xyz,
19.1.19
New JobCrypter Ransomware variant
MalwareHunterTeam found a new JobCrypter variant.
19.1.19
Looking for the Obfuscated Ransomware
![]()
Michael Gillespie is looking for a new ransomware that appends the .obfuscated extension and drops a ransom note named Read Me.txt.
19.1.19
New Anatova ransomware discovered
Valthek discovered a new ransomware called Anatova that asks for a ransom payment in Dash.
19.1.19
New ransomware variant
![]()
Petrovic found a new ransomware variant that appends the .jundmd@cock.li!! extension to encrypted files and drops a ransom note named Help to decrypt.txt.
19.1.19
BlackRouter Ransomware Promoted as a RaaS by Iranian Developer
A ransomware called BlackRouter has been discovered being promoted as a Ransomware-as-a-Service on Telegram by an Iranian developer. This same actor previousl distributed another ransomware called Blackheart and promotes other infections such as a RAT.
19.1.19
New 7Zip Ransomware variant
Amigo-A found a new variant of the 7Zip Ransomware that appends the .aes extension to encrypted files and drops a ransom note named INFORMATION.hta.
19.1.19
Xcry Ransomware discovered
MalwareHunterTeam discovered a new ransomware called Xcry that was programmed in Nim. Xcry Ransomware will append the .xcry7684 extension to encrypted files and drop a ransom note named HOW_TO_DECRYPT_FILES.html.
19.1.19
Oscar Venom Ransomware discovered
MalwareHunterTeam discovered a new Jigsaw Ransomware variant called Oscar Venom that appends the .venom extension to encrypted files.
19.1.19
Fake Jigsaw variants
MalwareHunterTeam discovered some new fake Jigsaw Ransomware variants that do not encrypt and have a password of "1212". They then display the "RUSSIAN FEDERATION ATTACKING YOU!" message when closing the program.
19.1.19
Jigsaw Ransomware has a loooong extension
Michael Gillespie found a new Jigsaw Ransomware sample that uses a very looooong extension.
19.1.19
New GIF Dharma variant
![]()
Jakub Kroustek found a new Dharma variant that appends the .gif extension to encrypted files.
19.1.19
StopDecryptor updated to support offline Djvu variants
Michael Gillespie updated his StopDecryptor to support newer .djvu variants.
19.1.19
Fallout Exploit Kit is Back with New Vulnerabilities and Payloads
![]()
The Fallout exploit kit is back in business after a short downtime, with new tools under its belt such as a new Flash exploit, HTTPS support, a new landing page format and the capability to deliver payloads using Powershell. One of its payloads is GandCrab.
19.1.19
New BitPaymer variant
GrujaRS found a new variant of BitPaymer that appends the .locked extension and drops a ransom note named [file_name].readme_txt
19.1.19
RickRoll Locker discovered
MalwareHunterTeam discovered anew ransomware called RICKROLL LOCKER that appends the .cryptoid extension and drops ransom notes named CRYPTOID_BLOCKED.txt, CRYPTOID_HELP.txt, and CRYPTOID_MESSAGE.txt. Appears to be a Aurora offline variant.
19.1.19
New James Ransomware
Leo found a new ransomware that appends the .James extension to encrypted files.
19.1.19
FileCryptor Ransomware discovered
Michael Gillespie found a new ransomware that drops a ransom note named HOW TO DECRYPT FILES.txt.
19.1.19
New Phobos Dharma variant
![]()
Coveware found a new variant of the Dharma ransomware that appends the .phobos extension to encrypted files.
13.1.19
Batch file ransomware discovered
MalwareHunterTeam discovered a very simply ransomware that is a batch file called Encoder.bat and uses WinRar to add files to a password protected archive.
13.1.19
GandCrab Operators Use Vidar Infostealer as a Forerunner
![]()
Cybercriminals behind GandCrab have added the infostealer Vidar in the process for distributing the ransomware piece, which helps increase their profits by pilfering sensitive information before encrypting the computer files.
13.1.19
Bridgeport Schools computer network falls victim to cyberattack
![]()
The city school district’s computer network was attacked Friday by a virus caused by an outside entity that intended to hold district data hostage for ransom, district officials say.
13.1.19
CryptoMix Ransomware Exploits Sick Children to Coerce Payments
![]()
With people becoming more aware of ransomware, criminals are coming up with some pretty low life schemes in order to coerce victims into paying ransomware. Such is the case with a CryptoMix ransomware, who pretends to represent a sick children's charity and is asking for a ransom payment as if it was a charitable donation.
13.1.19
Ryuk Ransomware Attack: Rush to Attribution Misses the Point
![]()
The most likely hypothesis in the Ryuk case is that of a cybercrime operation developed from a tool kit offered by a Russian-speaking actor. From the evidence, we see sample similarities over the past several months that indicate a tool kit is being used. The actors have targeted several sectors and have asked a high ransom, 500 Bitcoin. Who is responsible? We do not know. But we do know how the malware works, how the attackers operate, and how to detect the threat. That analysis is essential because it allows us to serve our customers.
13.1.19
The cyber-attack that sent an Alaskan community back in time
![]()
The BBC reports about the Ransomware attack that took out a town in Alaska. In 2018, a remote Alaskan community’s infrastructure was hit by a malware attack which forced it offline. It was only then they realised how much they depended on computers.
13.1.19
Ahihi Ransomware discovered
![]()
MalwareHunterTeam found the Ahihi ransomware does not change the extension.
13.1.19
Ransomware ransom note tries to phish PayPal account
![]()
MalwareHunterTeam found a new ransom note that also attempts to steal PayPal account credentials through a phishing page.
13.1.19
Possible new STOP/Djvu variant
![]()
Michael Gillespie is searching for a new Ransomware that appends the .pdff extension and drops a note named _openme.txt.
13.1.19
Del Rio City Hall Forced to Use Paper After Ransomware Attack
![]()
The City Hall of Del Rio, Texas was hit by a ransomware attack on Thursday, which led to multiple computers on the network being turned off and disconnected from the Internet to contain and analyze the malware.
13.1.19
Ryuk Ransomware Partners with TrickBot to Gain Access to Infected Networks
![]()
New research now indicates that the Ryuk actors may be renting other malware as an Access-as-a-Service to gain entrance to a network.
13.1.19
New STOP variants
![]()
Michael Gillespie noticed two new STOP variant that was uploaded to ID Ransomware and appends the .tfude or the .tro extensions to encrypted file names.
5.1.19
New MindSystemNotRansomware variant discovered
MalwareHunterTeam found a new MindSystemNotRansomWare variant that uses a new and interesting wallpaper.
5.1.19
New SeonRansomware distributed through Exploit kits
Vigilantbeluga discovered a new ransomware called SeonRansomware that is being distributed through Malvertising and the GreenFlashSundown exploit kit. This ransomware appends the .FIXT extension and drops a ransom note named YOUR_FILES_ARE_ENCRYPTED.txt and readme.hta.
5.1.19
Master Decryption Key Released for FilesLocker Ransomware
On December 29th, a Pastbin post was created that contains the master RSA decryption key for the FilesLocker Ransomware. The release of this key has allowed a decryptor to be created that can recover victim's files for free.
5.1.19
How to Decrypt the FilesLocker Ransomware with FilesLockerDecrypter
![]()
On December 29th, an unknown user released the master RSA decryption key for FilesLocker v1 and v2. This allowed Michael Gillespie to release a decryptor for files encrypted by the FilesLocker Ransomware that have the .[fileslocker@pm.me] extension appended to file names.
5.1.19
Cloud Hosting Provider DataResolution.net Battling Christmas Eve Ransomware Attack
![]()
According to Brian Krebs:
Cloud hosting provider Dataresolution.net is struggling to bring its systems back online after suffering a ransomware infestation on Christmas Eve, KrebsOnSecurity has learned. The company says its systems were hit by the Ryuk ransomware, the same malware strain that crippled printing and delivery operations for multiple major U.S. newspapers over the weekend.
5.1.19
Irish Rail Operator Gets Ransom Note on Its Website
![]()
The website of Luas.ie, the tram rail system operator in Dublin, Ireland, has been taken offline today after someone replaced its content with a ransom note demanding one bitcoin not to publish customer data.
5.1.19
FilesLocker 2.1 Released
MalwareHunterTeam discovered that FilesLocker v2.1 ransomware was released. This variant comes with a new RSA key, so it is no longer decryptable.
5.1.19
New decryptable ransomware discovered
![]()
MalwareHunterTeam discovered a ransomware that appends the .recovery_email_[retmydata@protonmail.com]_ID_[FCFABBBE].aes256 and is decryptable. If you are infected with this ransomware you can contact Michael Gillespie.
5.1.19
New B2DR Ransomware variant
![]()
Michael Gillespie.found a new variant of the B2DR Ransomware that appends the .artilkilin@tuta.io.wq2k extension to encrypted files.
5.1.19
How to Decrypt the Aurora Ransomware with AuroraDecrypter
The good news is that the variants of this ransomware family can be decrypted for free using a decryptor created by Michael Gillespie. In order to use the decryptor a victim just needs to have two encrypted files of a certain file type, which will be described later in the guide.
5.1.19
Another new Paradise Ransomware variant
MalwareHunterTeam found a new variant of the Paradise Ransomware that appends the "_%ID%_{alexbanan@tuta.io}.CORP" extension to encrypted files.
5.1.19
New Indrik Ransomware
Michael Gillespie found a new ransomware uploaded to ID Ransomware that appends the ".INDRIK" and drops a ransom note named "# HOW TO DECRYPT YOUR FILES #.html".
5.1.19
Boom Ransomware discovered
MalwareHunterTeam found the Boom Ransomware that tells you to contact a person on Facebook to get a PIN to decrypt the files. This is basically a front end to the Xorist ransomware.
5.1.19
Target777 Ransomware targeting businesses
![]()
Michael Gillespie found a new ransomware that is highly targeted as it includes a victim's name in the extension, emails, and ransom notes. The extensions also include the "777" digits. Michael thinks it may be based off of Defray.
5.1.19
Lockify Ransomware discovered
An in-development ransomware called Lockify was discovered by Leo that appends the .tunca extension to encrypted files.
5.1.19
New Paradise Ransomware version
Michael Gillespie found a new Paradise Ransomware variant that appends an extension with the pattern "__{}.VACv2" and drops a ransom note named "$%%! NOTE ABOUT FILES -=!-.html".
5.1.19
New LockCrypt 2.0 variant
Michael Gillespie found a new variant of the LockCrypt 2.0 ransomware that appends the extension " id-.LyaS" and drops a ransom note named "How To Restore Files.hta".
5.1.19
18 Months Later, WannaCry Still Lurks on Infected Computers
![]()
Eighteen months after the initial outbreak of the WannaCry Ransomware infection, the malware continues to rear its head on thousands, if not hundreds of thousands, of infected computers.
5.1.19
JungleSec Ransomware Infects Victims Through IPMI Remote Consoles
A ransomware called JungleSec is infecting victims through unsecured IPMI (Intelligent Platform Management Interface) cards since early November.
5.1.19
New Snatch Ransomware discovered
![]()
Michael Gillespie is looking for a sample of the Snatch Ransomware that appends the .snatch and drops a ransom note named Readme_Restore_Files.txt.
5.1.19
New Crysis Ransomware variant discovered
![]()
Jakub Kroustek discovered a new Dharma Ransomware variant that appends the .bizer extension to encrypted files.
5.1.19
AuroraDecryptor updated for Nano variant
![]()
Michael Gillespie updated the AuroraDecrypter to support the new .Nano variant. A guide on how to use it can be found here.
5.1.19
New Hidden Tear variant asks for 200 million yen.
MalwareHunterTeam found a new Hidden Tear variant that uses the extension .locked and asks for 200 million yen.
5.1.19
MMM Reborn
Michael Gillespie found a new TripleM variant called "MMM Reborn". The ransomware renames an encrypted file to hex and drops a ransom note named IF_YOU_NEED_FILES_READ_ME.html.
5.1.19
New nano Scarab Ransomware
![]()
Michael Gillespie found a new Scarab Ransomware variant that uses the extension .nano. This should not be confused with the Aurora variant that uses the upper case .Nano.
5.1.19
New GarrantyDecrypt variant
![]()
Michael Gillespie discovered a new variant of the GarrantyDecrypt Ransomware that appends the ".NOSTRO" or ".nostro" extensions and drops a ransom note named "#RECOVERY_FILES#.txt".
5.1.19
New Project57 Ransomware
Michael Gillespie discovered the Project57 Ransomware that uses the ".[ti_kozel@lashbania.tv].костя баранин" or ".[ti_kozel@lashbania.tv].êîñòÿ áàðàíèí", if the correct code page is not installed. The ransomware also drops ransom note names "DECRYPT.HTML" and "DECRYPT.txt".
5.1.19
Ryuk Ransomware Involved in Cyberattack Stopping Newspaper Distribution
![]()
A cyberattack reportedly bearing the signature of Ryuk ransomware caused disruption over the weekend in printing and delivery of major newspapers in the US from Tribune Publishing and Los Angeles Times.
5.1.19
New Ransomware hunt
![]()
Michael Gillespie is looking for a ransomware that appends the ".send.ID[redacted].to.dernesatiko@mail.com.crypted"extension and drops a note named "HOW TO DECRYPT FILES.txt".
22.12.18
GarrantyDecrypt Ransomware switch to a bizarre ransom note
MalwareHunterTeam found a new variant of the GarrantyDecrypt Ransomware utilizing a bizarre ransom note.
22.12.18
How to Decrypt HiddenTear Ransomware Variants
If you have been infected with a HiddenTear Ransomware variant, then you are in luck as a program called HiddenTearDecrypter has been created by Michael Gillespie that allows you to recover your encryption key without having to pay the ransom.
22.12.18
Jemd Ransomware discovered
@GrujaRS discovered a new ransomware called Jemd that drops a ransom note named Recovery.txt. According to Michael Gillespie, it does not properly encrypt files and the files are destroyed. fpgus1mx points out that the files can be recovered by Shadow Volume Copies, which are not wiped.
22.12.18
How to Decrypt the InsaneCrypt or Everbe 1 Family of Ransomware
InsaneCrypt or the Everbe 1.0 Ransomware is a family of ransomware infections that were based off of an open source project. This ransomware family is distributed through possibly spam and hacking into Remote Desktop Services, but it has not been confirmed.
22.12.18
PewDiePie Ransomware discovered
MalwareHunterTeam found what appears to be a joke ransomware named "PewDiePie" ransomware. Acts more like a screen locker.
22.12.18
New WormCrypt0r or WormCry Ransomware
![]()
Michael Gillespie found a new ransomware called WormCrypt0r or WormCry that appends the .WORMCRYPT0R extension to encrypted file names and drops a ransom note named WORMCRY.txt.
22.12.18
New Evolution Ransomware
Emmanuel_ADC-Soft found a new ransomware named Evoluion that appends the .evolution and drops a ransom note named !#_Read_me_for_revocery_#!.txt.
22.12.18
New Cypher Ransomware
S!Ri discovered the new Cypher Ransomware that drops ransom notes named HOW_TO_DECRYPT_FILES.rtf and HOW_TO_DECRYPT_FILES.html and appends the extension .cypher to encrypted file names.
22.12.18
GandCrab Ransomware devs trolling researchres
The GandCrab Ransomware devs appear to be releasing new versions with widely different version numbers in order to troll security researchers.
22.12.18
New aztecdecrypt Scarab variant
Emmanuel_ADC-Soft found a new Scarab Ransomware variant that appends the .aztecdecrypt@protonmail.com extension to encrypted files and drops a ransom note named HOW TO DECRYPT FILES.TXT.
22.12.18
New Matrix Ransomware variant
![]()
Michael Gillespie found a new Matrix Ransomware variant that appends the .PRCP extension and drops a ransom note named #README_PRCP#.rtf.
22.12.18
New Ransomwared Ransomware
Leo found a new ransomware called Ransomwared that uses DES encryption and is decryptable. When encrypting files it will append the .ransomwared extension to encrypted files.
22.12.18
BleepingComputer.com Is Now a Partner With No More Ransom!
![]()
BleepingComputer is humbled and honored to announce that we have joined No More Ransom project as an associate partner! We have been providing ransomware information, support, and the amazing decryptors from Michael Gillespie since the beginning and this partnership will enable more victims to receive the help they need.
22.12.18
New Russian Ransomware discovered
Petrovic discovered a new Russian ransomware that appends the .Защищено RSA-2048 extension to encrypted file names.
15.12.18
Sextortion Emails now Leading to Ransomware and Info-Stealing Trojans
![]()
Sextortion email scams have been a very successful way of generating money for criminals. A new Sextortion campaign is now taking it to the next level by tricking recipients into installing the Azorult information-stealing Trojan, which then downloads and installs the GandCrab ransomware.
15.12.18
EQ Ransomware discovered
GrujaRS discovered the EQ Ransomware that drops a ransom note named README_BACK_FILES.htm and uses .f**k (censored) as its extension for encrypted files. May be GlobeImposter.
15.12.18
New variants of the Gerber Ransomware discovered
Emmanuel_ADC-Soft discovered new variants of the Gerber Ransomware appending the .gerber5 and .FJ7QvaR9VUmi extensions.
15.12.18
Santa Dharma Ransomware variant
GrujaRS discovered a new variant of the Dharma Ransomware that appends the .[newsantaclaus@aol.com].santa extension to encrypted files.
15.12.18
New Crypto034 Scarab Ransomware variant
GrujaRS discovered a new Scarab Ransomware variant that appends the .crypted034 and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
15.12.18
Mercury Ransomware hunt
![]()
Michael Gillespie is looking for a new ransomware that appends the .Mercury extension and drops a ransom note named !!!READ_IT!!!.txt
15.12.18
New SYS CryptoMix variant
Michael Gillespie found a new CryptoMix variant that renames encrypted files to "[16 uppercase hex].SYS" and drops a ransom note named _HELP_INSTRUCTION.TXT.
15.12.18
Trojan and ransomware in the campaign impersonating InPost
![]()
From the translated Cert Polska article:
For the last few days we have been watching an e-mail campaign in which fake senders claim to be an InPost courier company. Messages inform about the shipment ready for pickup in one of the parcel machines. The address of the parcel locker and the pin needed to collect the parcel should be available after downloading the file from the link visible in the message. So far, we have distinguished two types of threats that await users after launching downloaded files. One of them is a Trojan that allows remote access to the victim's computer, and the other software that encrypts files - ransomware.
15.12.18
Fake WannaCry in circulation
M. Shahpasandi found a fake WannaCry ransomware that appends the .wannacry extension and drops a ransom note named Get Back FILES.txt.
15.12.18
Forma Ransomware
GrujaRS discovered the Polish Forma Ransomware that appends the .locked extension and drops a ransom note named ODSZYFRFUJ_PLIKI_TERAZ.txt.
15.12.18
Ransomware Hunt underway for Djvu Ransomware
![]()
Michael Gillespie found a new ransomware called Djvu that appends the .djvu extension and drops a ransom note named _openme.txt.
15.12.18
Ships infected with ransomware, USB malware, worms
![]()
For example, in an incident detailed in the report, a shipowner reported not one, but two ransomware infections, both occurring due to partners, and not necessarily because of the ship's crew.
15.12.18
New Ironhead Scarab Ransomware variant
![]()
Michael Gillespie found a new variant of the Scarab Ransomware that appends the .ironhead extension and drops a ransom note named How to restore encrypted files.txt.
8.12.18
GandCrab v5.0.9 comes with a message
Marcelo Rivero noticed that the GandCrab developers released version 5.0.9, which simply contains a message stating that "We will become back very soon! ;)"
8.12.18
New RISK Dharma Variant
![]()
Jakub Kroustek discovered a new Dharma Ransomware variant that appends the .RISK extension to encrypted files.
8.12.18
New IsraBye version
GrujaRS found a new version of the IsraBye ransoimware that appends the .israbye extension to encrypted files.
8.12.18
Dablio Ransomware discovered
Karsten Hahn found the new Dablio Ransomware that prepends "(encrypted)" to the beginning of encrypted file's name,
8.12.18
Ransomware Infects 100K PCs in China, Demands WeChat Payment
Over 100,000 thousand computers in China have been infected in just a few days with poorly-written ransomware named UNNAMED1989 that encrypts local files and steals credentials for multiple Chinese online services. This ransomware then asked victims to pay the developer via WeChat payments.
8.12.18
Company Pretends to Decrypt Ransomware But Just Pays Ransom
![]()
Security researchers from Check Point Research have found a company in Russia that guarantees decryption of files touched by the Dharma/Crisis ransomware strain, an operation known to be successful only by paying for the unlock key from the malware maker.
8.12.18
Atlanta U.S. Attorney Charges Iranian nationals for City Of Atlanta ransomware attack
![]()
A federal grand jury in Atlanta has returned an indictment charging Faramarz Shahi Savandi and Mohammed Mehdi Shah Mansouri with committing a sophisticated ransomware attack on the City of Atlanta in March 2018 in violation of the Computer Fraud and Abuse Act.
8.12.18
New bkpx Dharma Ransomware variant
![]()
Jakub Kroustek discovered a new Dharma Ransomware variant that appends the .bkpx extension to encrypted files.
8.12.18
Chinese Police Arrest Dev Behind UNNAMED1989 WeChat Ransomware
![]()
Chinese law enforcement have arrested the developer of the UNNAMED1989 / WeChat Ransomware that recently took China by storm and infected over 100K users in a few days.
8.12.18
Abandoned Globelmposter TOR Site Leaves Ransomware Victims Without Options
![]()
Recent victims of Globelmposter 2.0 found themselves grasping for a means to decrypt data after the TOR site in their ransomware notice was abandoned by its creators. In lieu of having backups, these victims have no path to decrypt their data or contact the hackers. Recent examples of the ransom notice left on encrypted machines appear below, and direct the user to a broken TOR site.
8.12.18
HiddenTear variant discovered
![]()
MalwareHunterTeam found a HiddenTear variant that tries to implicate a YouTuber who said he didn't make it. See the Twitter thread for more info.
8.12.18
Gerber Ransomware 1.0
Petrovic discovered the Gerber Ransomware 1.0 that appends the .XY6LR extension to encrypted file's names.
8.12.18
Gerber Ransomware 3.0
Soon after, GrujaRS discovered the Gerber Ransomware 3.0.
8.12.18
New LOL Scarab Ransomware variant
Amigo-A found a new variant of the Scarab Ransomware that appends the .lol extension to encrypted files and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
8.12.18
Outsider Ransomware discovered
GrujaRS discovered a ransomware called Outsider that appends the .protected extension.
8.12.18
JungleSec Ransomware uses open source encryption tool
![]()
Michael Gillespie learned from a victim that the JungleSec ransomware is utilizing the http://ccrypt.sourceforge.net/ encryption program.
1.12.18
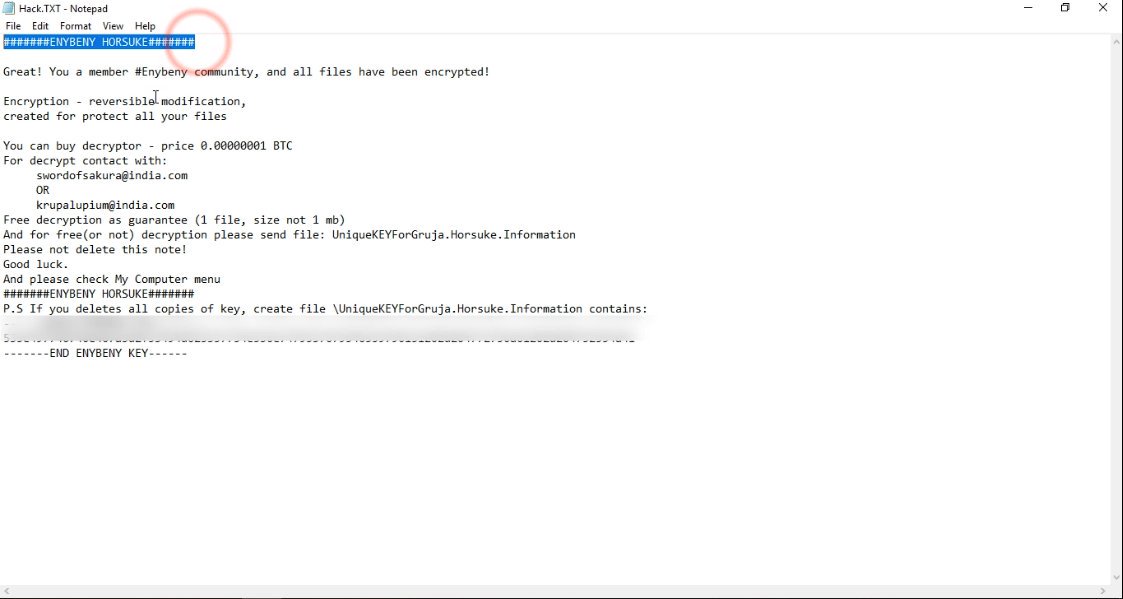
EnyBeny Nuclear Ransomware discovered
@GrujaRS discovered a new in-dev ransomware called EnyBeny Nuclear Ransomware that meant to append the extension .PERSONAL_ID:.Nuclear to encrypted files, but failed due to a bug.
1.12.18
New myjob Dharma variant
![]()
Jakub Kroustek discovered a new Dharma variant that appends the .myjob extension to encrypted files.
1.12.18
Lucky Ransomware discovered
![]()
Michael Gillespie discovered a new ransomware that renamed encrypted files to "[[email]][original].[random].lucky" and drops a ransom note named _How_To_Decrypt_My_File_.txt.
1.12.18
New Scarab Ransomware variants discovered
Emmanuel_ADC-Soft found a new Scarab Ransomware variant that appends the .lolita and drops a ransom note named _How to restore files.TXT and another variant that appends the .stevenseagal@airmail.cc extension and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
1.12.18
New Dharma variant discovered
Emmanuel_ADC-Soft discovered a new Dharma variant that appends the .[cyberwars@qq.com].war and drops a ransom note named FILES ENCRYPTED.txt.
1.12.18
New Dharma variant
![]()
Michael Gillespie discovered a new Dharma variant that appends the .risk extension to encrypted files.
1.12.18
GarrantyDecrypt Discovered
MalwareHunterTeam found the GarrantyDecrypt Ransomware that appends the .decryptgarranty extension to encrypted files and drops a ransom note named #RECOVERY_FILES#.txt.
1.12.18
New Everbe Ransomware variant
![]()
Michael Gillespie found a new Everbe 2.0 Ransomware variant that appends the .[].lightning extension to encrypted files.
1.12.18
New Scarab Ransomware variant
Emmanuel_ADC-Soft discovered another Scarab Ransomware variant that appends the .online24files@airmail.cc extension and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES-online24files@airmail.cc.TXT.
1.12.18
DOJ Indicts Two Iranian Hackers for SamSam Ransomware Operation
![]()
The Department of Justice announced today that a grand jury has unsealed an indictment against two Iranian hackers for conducting the hacking and ransomware operation called SamSam.
1.12.18
New GusCryptor discovered
S!Ri found a new ransomware called GusCryptor that appends the .bip extension. Note, the bip extension was also used by a Dharma Ransomware variant.
1.12.18
Making a Ransomware Payment? It May Now Violate U.S. Sanctions
![]()
Thinking about making a ransomware payment? If so, you may want to think twice before doing so as it could land you in trouble for violating U.S. government sanctions.
1.12.18
cmdRansomware Discovered
Petrovic found a new ransomware called cmdRansomware that utilizes a batch files and GPG to encrypt a computer. When encrypting it will append the .ransomware extension to encrypted files and drop a ransom note named cmdRansomware.txt.
1.12.18
Stop Ransomware decryptor released
Michael Gillespie released a free decryptor for the STOP Ransomware, which works on the .puma, .pumas, and .pumax variants.
1.12.18
Moscow's New Cable Car System Infected with Ransomware the Day After it Opens
![]()
Moscow recently opened its first cable-car service and promised free rides for the first month. Unfortunately, only two days after after the service was made available, attackers reportedly hacked into the cable car systems and infected them with ransomware.
24.11.18
Vapor Ransomware discovered
MalwareHunterTeam discovered the Vapor Ransomware that appends the .Vapor extension to encrypted files. Will delete files if you do not pay in time.
24.11.18
New EnyBenyHorsuke Ransomware discovered
GrujaRS discovered a new ransomware called EnyBenyHorsuke Ransomware that appends the .Horsuke extension to encrypted files.
24.11.18
New .fire Dharma variant
![]()
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .fire extension to encrypted files.
24.11.18
Dr. Web can reportedly decrypt the DCRTR ransomware
![]()
According to reports, Dr. Web can decrypt the DCRTR ransomware.
24.11.18
DeLpHiMoRix ransomware
Petrovic discovered a ransomware named DeLpHiMoRix.
24.11.18
New STOP Ransomware variant
Emmanuel_ADC-Soft found a new STOP Ransomware variant that appends the .INFOWAIT extension and drops a ransom note named !readme.txt.
24.11.18
Aurora / Zorro Ransomware Actively Being Distributed
A ransomware that has been distributed since the summer of 2018 has started to pick up steam in the latest variant. This new variant is currently being called Zorro Ransomware, but has also been called Aurora Ransomware in the past.
24.11.18
New CRYPTO Scarab variant
Emmanuel_ADC-Soft found a new Scarab Ransomware variant that appends the .CRYPTO extension to encrypted files and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
24.11.18
New STOP Ransomware variant
Marcelo Rivero found a new variant of the STOP Ransomware that appends the .PUMA extension to encrypted files and drops a ransom note named !readme.txt.
24.11.18
New Everbe Ransomware variant
MalwareHunterTeam found a new Everbe Ransomware variant that appends the .[yoursalvations@protonmail.ch].neverdies@tutanota.com extension to encrypted files and drops a ransom note named !=How_recovery_files=!.html.
24.11.18
New DelphiMorix pays homage to ransomware researchers
New variants of the DelphiMorix Ransomware were spotted that use .demonslay335 and .malwarehunterteam as the extension for encrypted files.
17.11.18
XUY Ransomware discovered
MalwareHunterTeam found a new ransomware called XUY that appends the extension .xuy to encrypted file's names.
17.11.18
Argus Ransomware discovered
Amigo-A found a new ransomware called Argus that appends the .ARGUS extension and drops a ransom note named ARGUS-DECRYPT.html.
17.11.18
Dharma Ransomware: What It’s Teaching Us
![]()
David Maciejak and Kenny Yongjian Yang of FortiGuard Labs take a look at Dharma Ransomware:
FortiGuard Labs has been monitoring the Dharma (also named CrySiS) malware family for a few years. As we demonstrate below even though the Dharma ransomware continues to be active, the attackers are not really updating their mode of operation, but continue to rely on a proven tactic to find and infect new victims, which is to leverage badly secured RDP services to gain access to the network.
17.11.18
XUY Ransomware discovered
MalwareHunterTeam found a new ransomware called XUY that appends the extension .xuy to encrypted file's names.
17.11.18
010001 Ransomware discovered
![]()
Michael Gillespie noticed a new ransomware, with a sample discovered by Jakub Kroustek, that appends the extension .010001 to encrypted files and drops a ransom note named tmpsfn_as.txt.
17.11.18
HookAds Malvertising Installing Malware via the Fallout Exploit Kit
![]()
The HookAds malvertising campaign has been active lately and redirecting visitors to the Fallout Exploit Kit. Once the kit is activated, it will attempt to exploit known vulnerabilities in Windows to install different malware such as the DanaBot banking Trojan, the Nocturnal information stealer, and GlobeImposter ransomware.
17.11.18
Titan Cryptor Discovered
![]()
MalwareHunterTeam discovered a new variant of the Argus Ransomware called Titan Cryptor. This variant does not add an extension and drops a ransom note name name Titan Instructions.html.
17.11.18
New SaveFiles Ransomware variant
MalwareHunterTeam found a new variant of the SaveFiles Ransomware called DataWait. This ransomware appends the .DATAWAIT extension and drops a ransom note named !readme.txt.
17.11.18
New Matrix variant
![]()
Michael Gillespie found a new variant of the Matrix Ransomware that appends the .FASTA extension and drops a ransom note named #README_FASTA#.rtf.
17.11.18
New .Back Dharma Ransomware variant
![]()
Michael Gillespie found a new variant of the Dharma Ransomware that appends the .back extension to encrypted files.
17.11.18
BlackHat Ransomware discovered
![]()
Michael Gillespie found a new ransomware uploaded to ID Ransomware that appends the .BlackHat extension to encrypted files and drops a ransom note named ReadME-BlackHat.txt.
17.11.18
New .Bear Dharma Ransomware variant
Jakub Kroustek discovered a new Dharma variant that appends the .Bear extension to encrypted files.
17.11.18
C3YPT3OR Ransomware discovered
MalwareHunterTeam found a new ransomware called C3YPT3OR that impersonates WannaCry.
10.11.18
M@r1a Ransomware discovered
MalwareHunterTeam discovered the M@r1a ransomware that appends the .mariacbc extension to encrypted files.
10.11.18
Kraken Cryptor 2.2 spread by Fallout exploit kit
Marcelo Rivero found Kraken Cryptor 2.2 being distributed through the Fallout Exploit Kit. The price changed from: 0.1 BTC to $80 dollars and the wallpaper changed to a Cerber style background.
10.11.18
New ransomware prepends enc
![]()
A new ransomware was discovered by Michael Gillespie that prepends the (enc) string to encrypted file names and drops a ransom note named aboutYourFiles.txt. For example, test.jpg would be encrypted and renamed to (enc)test.jpg.
10.11.18
New Dharma Ransomware variant
![]()
Michael Gillespie discovered a new Dharma Ransomware variant that appends the .adobe extension to encrypted files.
10.11.18
New Dharma Ransomware variant
Michael Gillespie found a new Dharma Ransomware variant that appends the .tron extension to encrypted files.
10.11.18
New Dharma Variant
![]()
Jakub Kroustek found two new Dharma Ransomware variants that append either the .AUDIT or .cccmn extension to encrypted files.
10.11.18
New PyCL Ransomware variant
Michael Gillespie found a new PyCL Ransomware variant that uses the .impect extension for encrypted files and drops a ransom note named how to get back you files.txt.
3.11.18
CommonRansom Ransomware Demands RDP Access to Decrypt Files
A new ransomware called CommonRansom was discovered that has a very bizarre request. In order to decrypt a computer after a payment is made, they require the victim to open up Remote Desktop Services on the affected computer and send them admin credentials in order to decrypt the victim's files. The ransomware appends the [old@nuke.africa].CommonRansom extension and drops a ransom note named DECRYPTING.txt.
3.11.18
New .XXXXX Dharma Variant
Jakub Kroustek discovered a new variant of the Dharma Ransomware that appends the .xxxxx and drops a ransom note named FILES ENCRYPTED.txt.
3.11.18
New Vendetta Ransomware
![]()
Michael Gillespie discovered the Vendetta Ransomware which renames files to hex and adds the .vendetta extension. It then drops a ransom note named How to decrypt files.txt. An example file name is 6F-12-09-78-15-FF-97-A4-49-66-F5-C6-81-00-3D-42.vendetta.
3.11.18
Kraken Ransomware 2.0.7 Released
MalwareHunterTeam found that Kraken Cryptor 2.0.7.1 beta was released and is demanding 1 BTC as the ransom.
3.11.18
Fallout Exploit Kit Releases the Kraken Ransomware on Its Victims
![]()
Rising from the deep, Kraken Cryptor ransomware has had a notable development path in recent months. The first signs of Kraken came in mid-August on a popular underground forum. In mid-September it was reported that the malware developer had placed the ransomware, masquerading as a security solution, on the website SuperAntiSpyware, infecting systems that tried to download a legitimate version of the antispyware software.
3.11.18
New Desktop Ransomware discovered
MalwareHunterTeam discovered the Desktop Ransomware, which prepends Lock. to filenames. Fly shared the pin number to unlock, which is "00114455220033669988554477++//".
3.11.18
New Ransomware using DiskCryptor With Custom Ransom Message
A new ransomware has been discovered that installs DiskCryptor on the infected computer and reboots your computer. On reboot, victims will be greeted with a custom ransom note that explains that their disk has been encrypted and to contact mcrypt18@yandex.com.
3.11.18
SimmyWare Ransomware Discovered
GrujaRS discovered a new ransomware called SimmyWare that appends the .SIMMYWARE extension and drops a ransom note named SIMMYWARE.txt.
27.10.18
New .betta Dharma Ransomware variant
![]()
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .betta extension to encrypted files.
27.10.18
Kraken Cryptor Ransomware Connecting to BleepingComputer During Encryption
![]()
Over the weekend, the Kraken Cryptor Ransomware released version 2.0.6, which now connects to BleepingComputer during different stages of their encryption process. It is not known what they are trying to achieve by doing this, but it does provide BleepingComputer with insight into the amount of victims being infected by this ransomware.
27.10.18
New Matrix Ransomware variant
![]()
Michael Gillespie found a new variant of the Matrix Ransomware that appends the .GMPF extension to encrypted files.
27.10.18
Solo Ransomware
Michael found a new ransomware that appends the .SOLO extension and drops a ransom note named IHRE_DATEIEN_SIND_VERSCHLUESSELT.html. Not the most sophisticated ransomware as it encrypts its own note.
27.10.18
Xorist continues with the long extensions
Michael Gillespie found another Xorist Ransomware variant that uses a crazy long extension.
27.10.18
HiddenBeer Ransomware discovered
GrujaRS discovered a new HiddenTear variant called HiddenBeer that appends the .beer extension to encrypted files.
27.10.18
New .Vanss Dharma variant
Jakub Kroustek found a new Dharma Ransomware variant that appends the .vanss extension and drops a ransom note named Info.html and FILES ENCRYPTED.txt.
27.10.18
Free Decrypter Available for the Latest GandCrab Ransomware Versions
A newly released decryptor allows for the free recovery of files encrypted by GandCrab versions 1, 4, and 5.
27.10.18
New FilesLocker Ransomware Offered as a Ransomware as a Service
A new ransomware called FilesLocker is being distributed as a Ransomware as a Service, or RaaS, that targets Chinese and English speaking victims.
27.10.18
ESET releases new decryptor for Syrian victims of GandCrab ransomware
![]()
ESET experts have created a new decryption tool that can be used by Syrian victims of the GandCrab ransomware. It is based on a set of keys recently released by the malware operators
27.10.18
New .Funny Dharma variant
![]()
Michael Gillespie found a new Dharma Ransomware variant that appends the .FUNNY extension to encrypted files.
27.10.18
New Everbe 2.0 variant
![]()
Michael Gillespie found a new variant of the Everbe 2.0 Ransomware that appends the .[everest@airmail.cc].EVEREST and drops ransom note named EVEREST LOCKER .txt and 新建文本文档.txt.
27.10.18
ID Ransomware adds extortion scam detections
![]()
Michael Gillespie added detections for extortion scam emails.
27.10.18
GandCrab 5.0.5 released that breaks free decryption
![]()
Tamas Boczan discovered that GandCrab v5.0.5 was released, which breaks the free decryption through Bitdefender's recently released decryptor.
27.10.18
New Ransomware
S!Ri discovered a new ransomware that appends the .docx extension to encrypted files.
20.10.18
GandCrab redesigns their ransom page
Damian1338 noticed that GandCrab did a major redesign of the payment page.
20.10.18
EbolaRnsmwr discovered
MalwareHunterTeam discovered a new in-dev ransomware called EbolaRnsmwr that appends the .101 extension and is based off of HiddenTear.
20.10.18
New Dharma variant
#CrySiS #Ransomware extension .[mixon.constantine@aol.com].gamma!Ransom note; all your data has been locked us You want to return? write email mixon.constantine@aol.com or mclainmelvin@aol.com https://youtu.be/Xkd4m6GqeO4
20.10.18
New Scarab variant
![]()
Amigo-A found a new variant of the Scarab Ransomware that appends the .DD extension to encrypted files and drops a ransom note named HOW TO RETURN FILES.TXT.
20.10.18
New Crypton Ransomware discovered
![]()
GrujaRS discoverd a new ransomware called Crypton that a ransom note named README.TXT.
20.10.18
New CryptoConsole Variant
Amigo-A found a new variant of the CryptConsole-3 Ransomware that does not add an extension and drops a ransom note named README.txt.
20.10.18
New District ransomware
![]()
Michael Gillespie found a new ransomware that appends the .ctrlalt@cock.li.district extension to encrypted files and drops a ransom note named READ_IT.district.
20.10.18
New Scarab Ransomware variant
Amigo-A found a new Scarab Ransomware variant that appends the .yourhope@airmail.cc extension and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
20.10.18
New EqutionDrug variant
Michael Gillespie found a new ransomware appending the .katyusha and dropping a ransom note named _how_to_decrypt_you_files.txt. Kaspersky detects this as an "EquationDrug" variant.
20.10.18
New Matrix Ransomware variant
![]()
Michael Gillespie found a new Matrix Ransomware variant that appends the .THDA extension and drops a ransom note named !README_THDA!.rtf.
20.10.18
GandCrab Devs Release Decryption Keys for Syrian Victims
![]()
In a post to an underground hacking and cybercrime forum, the GandCrab developers have released the decryption keys for Syrian victims.
20.10.18
Birbware Ransomware discovered
MalwareHunterTeam discovered a new ransomware called Birbware that adds the .birbb extension to encrypted files and states that you can get a free decryption key by contacting the developer on Discord.
20.10.18
Ransomware masquerading as a Fortnite vBucks hack
MalwareHunterTeam discovered a fake ransomware pretending to be a Fortnite vBucks hack.
13.10.18
God Crypt Joke Ransomware
![]()
MalwareHunterTeam found a new ransomware called God Crypt that does not appear to decrypt and appears to be a joke ransomware. Has an unlock code of 29b579fb811f05c3c334a2bd2646a27a.
13.10.18
New Dharma Ransomware variant
![]()
Michael Gillespie found a new Dharma Ransomware variant that appends the .boost extension to encrypted files uploaded to ID Ransomware.
13.10.18
New Matrix Ransomware variants
![]()
Michael Gillespie found a new Matrix Ransomware variant that appends the .GMAN and drops a ransom note named !README_GMAN!.rtf uploaded to ID Ransomware. Michael also found a variant that appends .EMAN50 and drops a note named #README_EMAN50#.rtf.
13.10.18
New Scarab Ransomware variant
![]()
Michael Gillespie found a new Scarab Ransomware variant that uses the extension .[crab7765@gmx.de].crab and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
13.10.18
New Possible Scarab variant
![]()
Michael Gillespie found a new ransomware that may be a Scarab variant that appends the .qweuirtksd extension to encrypted files and drops a ransom note named !!!ReadMeToDecrypt.txt. There are victims on BleepingComputer.
13.10.18
New DecryptFox Ransomware
![]()
Michael Gillespie found a new ransomware uploaded to ID Ransomware that appends the .encr extension and drops a ransom note named readmy.txt.
13.10.18
Windows 10 Ransomware Protection Bypassed Using DLL Injection
![]()
At the DerbyCon security conference last week, a security researcher showed how DLL injection can be used by ransomware to bypass the Controlled Folder Access ransomware protection feature.
13.10.18
GandCrab Vaccine continues to work with version 5.0.3
![]()
Valthek's vaccine for GandCrab continues to work with the release of version 5.0.3.
13.10.18
Rapidly Evolving Ransomware GandCrab Version 5 Partners With Crypter Service for Obfuscation
The GandCrab ransomware, which first appeared in January, has been updated rapidly during its short life, with Version 5.0.2 appearing this month. In this post we will examine the latest version and how the authors have improved the code (and in some cases have made mistakes).
13.10.18
Council hit by cyber attack reveals £2m cost
![]()
The BBC reports:
Copeland Borough Council has revealed that an attack on its systems in August 2017 has cost it about £2m.
The hack locked staff out of a number of council services, including payroll, planning and environmental health.
13.10.18
The ransomware with most annoying extension
Michael Gillespie found a new RotorCrypt variant that uses the most annoying extension I have ever seen. This extension is "!@#$%^&-()_+.1C" and the ransom note is INFO.txt.
13.10.18
New garrantydecrypt Ransomware
![]()
Michael Gillespie found a new ransomware that appends the .garrantydecrypt extension and drops a ransom note named #RECOVERY_FILES#.txt.
13.10.18
New Matrix Ransomware variant
![]()
Michael Gillespie found a new variant of the Matrix Ransomware that appends the .NOBAD extension and drops a ransom note named #NOBAD_README#.rtf.
13.10.18
New Backdoor Ties NotPetya and Industroyer to TeleBots Group
Security researchers found the missing link that helps them prove that the NotPetya disk-wiping malware and the Industroyer backdoor for electric power systems are the work of the TeleBots group.
13.10.18
New Dharma Ransomware variant
![]()
Jakub Kroustek discovered a new Dharma Ransomware variant that appends the .[Darknes@420blaze.it].waifu extension.
13.10.18
WannaCash decryptor updated with new variant
![]()
Alex Svirid updated his WannaCash decryptor for a new variant that changes the file name to "зашифровано original_name".
7.10.18
New Matrix Ransomware variant
![]()
Michael Gillespie discovered a new variant of the Matrix Ransomware that appends the .EMAN extension and drops a ransom note named #README_EMAN#.rtf.
7.10.18
New Unlock92 variant
![]()
Michael Gillespie found a new variant of the Unlock92 Ransomware that appends the .@LOCKED extension and drops a ransom note named .txt.
7.10.18
New Dharma variant
Jakub Kroustek found a new CrySiS/Dharma variant that appends the .btc extension and drops ransom notes named Info.hta and FILES ENCRYPTED.txt.
7.10.18
Hackers demand bitcoin ransom in cyberattack on big Canadian restaurants
![]()
A Canadian company that owns many popular restaurant chains has been told to pay ransom in bitcoin to retrieve data that hackers claim to have stolen.
7.10.18
Fallout Exploit Kit Now Installing the Kraken Cryptor Ransomware
The Fallout Exploit has been distributing the GandCrab Ransomware for the past few weeks, but has now switched its payload to the Kraken Cryptor Ransomware.
7.10.18
New Dharma variant
![]()
Jakub Kroustek found a new CrySiS/Dharma variant that appends the .bgtx extension and drops ransom notes named Info.hta and FILES ENCRYPTED.txt.
29.9.18
Qinynore Ransomware discovered
Karsten Hahn has discovered a new HiddenTear variant called Qinynore Ransomware. This ransomware appends the .anonymous extension to encrypted files and drops a ransom note named YOU_MUST_READ_ME.rtf .
29.9.18
Bytar Ransomware discovered
Karsten Hahn discovered a new ransomware called Bytar that appears to be in development.
29.9.18
New LockCrypt 2.0 variant
GrujaRS discovered a new LockCrypt 2.0 variant that appends the .BDKR extension to encrypted files and creates a ransom note named How To Restore Files.txt.
29.9.18
XD Ransomware
![]()
GrujaRS discovered a ransomware appending the .xd extension to encrypted files.
29.9.18
Pennsylvania Senate Democrats paid $700,000 to recover from ransomware attack
![]()
Microsoft was paid $703,697 to help Pennsylvania Senate Democrats rebuild IT systems after 2017 ransomware incident.
29.9.18
New Jigsaw Ransomware variant
![]()
Michael Gillespie found a new Jigsaw Ransomware targeting German victims and appending the .spaß extension to encrypted files.
29.9.18
GandCrab V5 Released With Random Extensions and New HTML Ransom Note
GandCrab v5 has been released with a few noticeable changes. The most noticeable changes are that the ransomware now uses a random 5 character extension for encrypted files and has a HTML ransom note.
29.9.18
GandCrab v5 Ransomware Utilizing the ALPC Task Scheduler Exploit
The GandCrab v5 ransomware has started to use the recently disclosed Task Scheduler ALPC vulnerability to gain System privileges on an infected computer. This vulnerability was recently patched by Microsoft in the September 18 Patch Tuesday, but as shown by computers still vulnerable to EternalBlue, business can be slow to install these updates.
29.9.18
Port of San Diego Affected by a Ransomware Attack
![]()
On September 25th, the Port of San Diego announced that their information technology systems had been disrupted by a cyber attack. In an announcement today, it was announced that this disruption was caused by a ransomware attack.
29.9.18
IC3 Issues Alert Regarding Remote Desktop Protocol (RDP) Attacks
![]()
The Internet Crime Complaint Center (IC3), in collaboration with the Department of Homeland Security and the FBI, have issued a security alert regarding attacks being conducted through the Windows Remote Desktop Protocol. While the most publicized attacks over RDP are related to ransomware, attackers also hack into exposed RDP services for corporate theft, installation of backdoors, or as a launching point for other attacks.
22.9.18
New Brrr Dharma Ransomware Variant Released
A new variant of the Dharma Ransomware was released this week that appends the .brrr extension to encrypted files. This variant was first discovered by Jakub Kroustek who tweeted a link to the sample on VirusTotal.
22.9.18
Ransomware attack blacks out screens at Bristol Airport
![]()
Flight information screens were blacked out over the weekend at the Bristol Airport in the UK. Airport officials blamed the incident on a ransomware infection that affected the computers running the airport's in-house TV screens displaying arrival and departure flight information.
22.9.18
New IT.Books ransomware
MalwareHunterTeam discovered a new HiddenTear variant called IT.Books Ransomware that looks like Jigsaw. Drops a ransom note named READ__IT.txt and extension of .f*cked. See the tweet for the uncensored extension.
22.9.18
New Everbe 2.0 variant
![]()
Michael Gillespie found a new variant of the Everbe 2.0 Ransomware that appends the ".[].NOT_OPEN" and drops a ransom note named "!_HOW_RECOVERY_FILES_!.txt".
22.9.18
New Matrix ransomware variants
![]()
Michael Gillespie found a new variant of the Matrix Ransomware that renames files to "[che808@protonmail.com].-.CHE808". Michael also found another variant that renames files to "[KOK08@QQ.COM].-.CHE08".
22.9.18
Xbash Malware Deletes Databases on Linux, Mines for Coins on Windows
What may very well be considered a cybercriminal's dream tool is now real and it is hunting Windows and Linux servers: a botnet with self-spreading capabilities that combines cryptomining and ransomware functions.
22.9.18
Database with 11 Million Email Records Exposed
A huge customer database containing 11 million records that include personal details, has been discovered on Monday sitting online, unprotected.
22.9.18
No personal info lost in ransomware attack, says VON Canada
![]()
CBC reported that "VON Canada is assuring clients and staff that their information is safe after the nursing organization was the target of a ransomware incident earlier this month."
22.9.18
Allscripts files a Motion to Dismiss for the ransomware related lawsuit
![]()
Allscripts was sued by customers for an outage caused by the SamSam ransomware. They have not filed a Motion to Dismiss to get the lawsuit thrown out.
22.9.18
Possible new Dcrtr Ransomware variant spotted
![]()
Michael Gillespie noticed a possible new Dcrtr variant that appends the .[].parrot extension and drops a ransom note named ReadMe_Decryptor.txt.
22.9.18
New Scarab variant
![]()
Amigo-A found a new variant of the Scarab Ransomware that appends the .skype extension to encrypted files and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
22.9.18
Romanian Woman Admits Involvement in Hacking Attack On Washington Police Computers
![]()
A Romanian woman admitted on Thursday her participation in a ransomware distribution scheme that ended up disabling computers used by the Washington D.C. police for surveillance.
22.9.18
Gamma, Bkp, & Monro Dharma Ransomware Variants Released in One Week
This week Jakub Kroustek found three new Dharma Ransomware variants that append either the .Gamma, .Bkp, & .Monro extensions to encrypted files.
22.9.18
NSA Codebreaker Challenge Started
The NSA CodeBreaker Challenge started today and this year has a theme revolving around ransomware.
22.9.18
Scottish brewery recovers from ransomware attack
![]()
Staff at Arran Brewery were locked out of its computer systems this week following a ransomware attack.
The attack against the Isle of Arran-based Scottish beer maker appears to have been a targeted strike. Prior to the infection, adverts for an already filled finance post at the brewery were placed on recruitment sites worldwide. This, in turn, resulted in an influx of CVs.
15.9.18
New Brr Dharma variant
Jakub Kroustek discovered a new variant of the Dharma ransomware that appends the .brrr extension and drops a ransom note named Info.hta
15.9.18
MVP Ransomware discovered
Siri discovered a new ransomware that is appending the .mvp extension to encrypted files.
15.9.18
New Scarab Ransomware variant
Amigo-A found a new variant of the variant Scarab-DiskDoctor ransomware that uses the .mammon extension for encrypted files. Emmanuel_ADC-Soft shared the ransom note below. Other new Scarab variants found this week append the extensions : .omerta and .bomber.
15.9.18
Mongo Lock Attack Ransoming Deleted MongoDB Databases
![]()
An attack called Mongo Lock is targeting remotely accessible and unprotected MongoDB databases, encrypting them, and then demanding a ransom in order to get the contents back.
15.9.18
New Matrix Ransomware variant
![]()
Michael Gillespie found a new Matrix Ransomware variant that uses appends the .ITLOCK extension to encrypted files and drops a ransom note named !ITLOCK_README!.rtf.
15.9.18
StorageCrypter still alive
![]()
Michael Gillespie noticed numerous submissions to ID Ransomware from South Korea for the StorageCrypter ransomware. This version is using a new ransom note named read_me_for_recover_your_files.txt.
15.9.18
Kraken Cryptor Ransomware Masquerading as SuperAntiSpyware Security Program
The Kraken Cryptor Ransomware is a newer ransomware that was released in August 18. A new version, called Kraken Cryptor 1.5, was recently released that is masquerading as the legitimate SuperAntiSpyware anti-malware program in order to trick users into installing it.
15.9.18
Fallout Exploit Kit Pushing the SAVEfiles Ransomware
Last week the Fallout Exploit kit was distributing the GandCrab ransomware. This week, it has started to distribute a new ransomware called SAVEfiles, for lack of a better name, through malvertising campaigns.
15.9.18
New Rektware ransomware
GrujaRS discovered a new ransomware called Rektware that appends the .CQScSFy extension.
14.9.18
The Kraken Ransomware is a newer ransomware that was released in August 18. A new version, called Kraken 1.5, was recently released that is masquerading as the legitimate SuperAntiSpyware anti-malware program in order to trick users into installing it.
12.9.18
Barack Obama's Blackmail Virus Ransomware Only Encrypts .EXE Files
Every once in a while you come across a really strange malware and such is the case with a new ransomware that only encrypts .EXE files on a computer. It then displays a screen with a picture of President Obama that asks for a "tip" to decrypt the files.
12.9.18
Locdoor Ransomware discovered
Leo discovered a new ransomware called Locdoor/DryCry. May be bugger or in development as it does not encrypt all files. When it does encrypt, it will append the .door[random number] extension to encrypted files.
12.9.18
New PyLocky variant
CyberSecurity found a new PyLocky variant that appends the .lockedfile and .lockymap extension to encrypted files and drops a ransom note named LOCKY-README.txt.
12.9.18
New Ransomware targeting servers
A new ransomware has been discovered by dave that appears to be targeting web servers. It is unknown what extension, if any, is appended to encrypted files.
12.9.18
New Matrix Ransomware variant
![]()
Michael Gillespie found a new Matrix Ransomware variant that appends the .FASTBOB extension and drops a ransom note named #_#FASTBOB_README#_#.rtf. Michael discovered another variant that appends the .NEWRAR extension and drops a note named #NEWRAR_README.rtf.
12.9.18
New Shiva Ransomware variant
MalwareHunterTeam found a new Shiva variant with active victims that appends the .good extension and drops a ransom note named HOW_TO_RECOVER_FILES.txt.
12.9.18
New CryptoJoker variant
![]()
Michael Gillespie found the decrypter for a new CryptoJoker variant that uses the .partially.cryptolocker and .fully.cryptolocker.
12.9.18
YARA Rule created for Shrug2
![]()
Marc Rivero López created a new YARA rule that detects the Shrug2 ransomware based on an article from Quick Heal.
12.9.18
New Fallout Exploit Kit Drops GandCrab Ransomware or Redirects to PUPs
A new exploit kit called Fallout is being used to distribute the GandCrab ransomware, malware downloading Trojans, and other potentially unwanted programs (PUPs).
12.9.18
New yyy0 Ransomware
![]()
Michael Gillespie found a new ransomware that appends the .davilarita@mail.com.yyy0 extensio and drops a ransom note named help.txt.
12.9.18
New Bandarchor variant adds .pip
Jakub Kroustek found a new Bandarchor ransomware variant that appends the .id-%ID%-[shivamana@seznam.cz].pip extension to encrypted files.
12.9.18
New Matrix Ransomware variant
![]()
Michael Gillespie saw a new Matrix Ransomware variant uploaded to ID Ransomware tha uses the .KOK08 extension and the ransom note #KOK08_README#.rtf.
12.9.18
New EOEO AutoIt ransomware
MalwareHunterTeam has found the EOEO AutoIt ransomware that appends the .eoeo extension to encrypted files.
12.9.18
New 5H311 1NJ3C706 Ransomware
Michael Gillespie found a new ransomware called 5H311 1NJ3C706 that acts more like a screenlocker, but does have encryption code that adds the extension .5H11 1NJ3C706, but does not appear to be working. . The password to the screenlocker is 666HackerThn.
12.9.18
New Suri Ransomware
MalwareHunterTeam found a new ransomware called Suri that appends the .SLAV extension. It is based on Stupid Ransomware.
4.9.18
CreamPie Ransomware discovered
Jakub Kroustek found what appears to be an in-dev version of the CreamPie Ransomware. It does not currently display a ransom note, but does encrypt files and appends the .[backdata@cock.li].CreamPie extension to them.
4.9.18
Jeff the Ransomware
Leo discovered the Jeff the Ransomware variant. Looks to be in-development as it does not encrypt.
4.9.18
New Matrix Ransomware variant
![]()
Michael Gillespie found a new Matrix Ransomware variant that renames files in the format "[KOK8@protonmail.com].-.KOK8" and drops a ransom note named #KOK8_README#.rtf.
4.9.18
New Cassetto Ransomware
Michael Gillespie saw an encrypted file uploaded to ID Ransomware that appends the .cassetto extension and drops a ransom note named IMPORTANT ABOUT DECRYPT.txt.
4.9.18
Acroware Screenlocker
Leo discovered a screenlocker that calls itself Acroware Cryptolocker Ransomware. It does not encrypt.
4.9.18
Termite Ransomware discovered
Ben Hunter discovered a new ransomware called Termite Ransomware. When encrypting a computer it will append the .aaaaaa extension to encrypted files.
4.9.18
New LockCrypt Variant
MalwareHunterTeam found a new LockCrypt variant that appends the .BadNews extension to encrypted files and drops a ransom note named How To Decode Files.hta.
4.9.18
CryptoNar Ransomware
MalwareHunterTeam found a new CryptoJoker variant called CryptoNar that appends either the .fully.cryptoNar or .partially.cryptoNar extension to encrypted files and drops a ransom note named CRYPTONAR RECOVERY INFORMATION.txt. Michael Gillespie created a decryptor for this variant.
4.9.18
New Pico Ransomware
S!Ri found a new Thanatos Ransomware variant called PICO Ransomware. This ransomware will append the .PICO extension to encrypted files and drop a ransom note named README.txt.
4.9.18
CryptoNar Ransomware Discovered and Quickly Decrypted
This week a new CryptoJoker ransomware variant was discovered called CryptoNar that has infected victims. The good news, is that a free decryptor was quickly released so that these victims can get their files back for free.
29.8.18
AZORult Trojan Serving Aurora Ransomware by MalActor Oktropys
![]()
Towards the end of July 18, we saw a new version of the AZORult trojan being used in malware campaigns targeting computers globally. In this article, we will dive into the malware and analyze its execution flow and payloads.
29.8.18
Beware of Spam with Fake Invoices Pushing Hermes 2.1 Ransomware and AZORult
A malspam campaign is underway that pretends to be an invoice for an outstanding payment. When these invoices are opened they install the AZORult information stealing Trojan and the Hermes 2.1 Ransomware onto the recipient's computer.
29.8.18
New Fox Ransomware Matrix Variant Tries Its Best to Close All File Handles
A new variant of the Matrix Ransomware has been discovered that is renaming encrypted files and then appending the .FOX extension to the file name. Of particular interest, this ransomware could have the most exhaustive process of making sure each and every file is not opened and available for encrypting. Thankfully, this also makes its encryption process very slow so it could be easier to detect.
29.8.18
New TorchWood Ransomware Variant
Amigo-A found a new variant of the Russian TorchWood ransomware that uses the .TRCHWD extension for encrypted files and is installed over RDP.
29.8.18
New NinjaLock Ransomware
MalwareHunterTeam found a new ransomware called NinjaLock. Jack shared the image and stated it does not encrypt.
29.8.18
New Creeper Ransomware variant
Amigo-A found a new variant of the Creeper Ransomware variant that appends the .crypton extension and drops a ransom note named DECRIPT_FILES.txt.
29.8.18
New Jigsaw variant with new background
Michael Gillespie found a new Jigsaw Ransomware variant that uses the .fun extension and the following background image.
29.8.18
New Scarab Ransomware variant
![]()
Michael Gillespie found a new Scarab Ransomware variant that utilizes the .CYBERGOD extension and another that uses the .rent extension.
29.8.18
Ryuk Ransomware Crew Makes $640,000 in Recent Activity Surge
A new ransomware strain named Ryuk is making the rounds, and, according to current reports, the group behind it has already made over $640,000 worth of Bitcoin.
29.8.18
New RotorCrypt Ransomware
![]()
Michael Gillespie found a new RotorCrypt Ransomware variant that appends the !@#$_(decryp in the EMail)____nautilus369alarm@gmail.com____$#@..AlfaBlock extension to encrypted files.
29.8.18
New Rapid Ransomware v1 Variant
MalwareHunterTeam found a new Rapid v1 Ransomware variant that now uses the .no_more_ransom extension on encrypted files.
29.8.18
New Xorist variant discovered
Michael Gillespie found a new Xorist Ransomware variant that uses the extensions .PrOtOnIs and .PrOtOnIs.VaNdElIs.
29.8.18
New n1n1n1 ransomware variant
![]()
Michael Gillespie noticed a new n1n1n1 variant uploaded to ID Ransomware that uses the "jpa." prefix on files and drops a ransom note named why files renamed jpa..txt.
29.8.18
New Why Ransomware discovered
![]()
Michael Gillespie noticed a new ransomware variant uploaded to ID Ransomware that uses the .WHY extension and drops a ransom note named !!!WHY_MY_FILES_NOT_OPEN!!!.txt.
29.8.18
New TotalWipeOut ransomware
MalwareHunterTeam found a new ransomware called TotalWipeOut.
29.8.18
New PyLocky variant
MalwareHunterTeam found a new PyLocky variant that appends the .lockedfile extension to encrypted files.
29.8.18
New Oni Ransomware variant
MalwareHunterTeam found a new Oni Ransomware variant that drops ransom notes named RESTORE_ONI_FILES.txt and renamed files to the "%original file name (incl. extension) converted to hex%.ONI" format.
29.8.18
New Jigsaw Ransomware variant
![]()
Michael Gillespie found a new Polish Jigsaw Ransomware variant that appends the extension .#__EnCrYpTED_BY_dzikusssT3AM_ransomware!__#.
23.8.18
At least three organizations in the United States and worldwide have been severely affected, the attackers are estimated to have already netted over $640,000 to date. The malicious code used in the attack was tracked as Ryuk ransomware, it appears connected to Hermes malware that was associated with the notorious Lazarus APT group. “Curiously, our research lead us to connect the nature of Ryuk’s campaign and some of its inner-workings to the HERMES ransomware, a malware commonly attributed to the notorious North Korean APT Lazarus Group, which was also used in massive targeted attacks.”
22.8.18
Bunch of Jigsaw Ransomware variants released.
![]()
Michael Gillespie discovered a bunch of new Jigsaw Ransomware variant released this week. These variants add the .hacked.by.Snaiparul, .lockedgood, and .pleaseCallQQ. He also noticed a .fun variant that asks for amazon gift cards as a payment.
22.8.18
New FSociety Themed Ransomware
MalwareHunterTeam discovered a new ransomware with a Fsociety theme that appends the .ShutUpAndDance extension to encrypted files.
22.8.18
Wise Ransomware discovered
MalwareHunterTeam discovered a ransomware named Wise Ransomware that does not encrypt anything, but rather deletes the files.
22.8.18
New SARansom Ransomware discovered
MalwareHunterTeam discovered a new in-dev ransomware called SARansom ransomware. Asks for a very aggressive amount of bitcoins. "For the low fee of 5 bitcoin"
22.8.18
Princess Evolution Ransomware is a RaaS With a Slick Payment Site

A new variant of the Princess Locker ransomware is being distributed called Princess Evolution. Like its predecessor, Princess Evolution is a Ransomware as a Service, or RaaS, that is being promoted on underground criminal forums.
22.8.18
Former Microsoft Engineer Gets 18 Months in Prison for Role in Ransomware Scheme
On Monday, a Florida judge sentenced a former Microsoft network engineer to 18 months in prison for his role in helping launder money obtained from victims of the Reveton ransomware.
22.8.18
New Jobcrypter variant
MalwareHunterTeam discovered a new JobCrypter ransomware variant that continues to target French victims, but now asks for $1000€.
22.8.18
Hermes 2.1 RaaS promoted on underground forums
Damian1338 found Hermes 2.1 Ransomware RaaS being promoted on underground criminal forums.
22.8.18
MAFIA ransomware targeting users in Korea
A new ransomware family was discovered and sent to me by MalwareHunterTeam, which we'll call MAFIA due to the extension it uses to encrypt files. The ransomware appears to target users in Korea, and may have been developed with at least knowledge of the Korean language.
22.8.18
Golden Ransomware discovered
Bart found a new ransomware called Golden Ransomware. Appears to be in-dev and doesn't actually encrypt.
22.8.18
New Cmb Dharma Ransomware Variant Released
On Thursday a new variant of the Dharma Ransomware was discovered that appends the .cmb extension to encrypted files.
10.8.18
![]()
MalwareHunterTeam found a new in-development Hidden Tear variant called PooleZoor ransomware that appends the .poolezoor extension to encrypted files.
10.8.18
A new distribution campaign is underway for a STOP Ransomware variant called KeyPass based on the amount of victims that have been seen. Unfortunately, how the ransomware is being distributed is unknown at this time.
9.8.18
![]()
Michael Gillespie found a new variant of the Dharma Ransomware that appends the .id-.[].cmb extension to encrypted files.
9.8.18
MalwareHunterTeam found a new ransomware called ZOLDON Crypter V3.0.
8.8.18
![]()
According to a report from GolfWeek, computers at the PGA of America’s offices have been infected with ransomware. The victims learned they were infected on Tuesday when ransom notes started appearing on their screen.
8.8.18
MalwareHunterTeam found a new ransomware named RansomWarrior 1.0 that renames encrypted files to the format "Encrypted%# of file%.THBEC".
7.8.18
Michael Gillespie found a Jigsaw Ransomware variant that appends the .dat extension to encrypted files and uses the following background.
7.8.18
Damian1338 saw Rapid Ransomware RaaS being sold on underground Russian forums.
6.8.18
New RewyWare Ransomware
S!Ri discovered a new ransomware named RetwyWare that appends the .killrabbit extension to encrypted files.
6.8.18
Jawe found a modified version of GandCrab v4.3 that has a version of 4.4 set. According to Jawe, all it does it set the Global\885BDEB9D36E550F587C.lock mutex and then sleeps. While we are not 100% sure if it was released by the GandCrab group, knowing their sense of humor it wouldn't surprise us.
3.8.18
New Everbe 2.0 variant
![]()
Michael Gillespie discovered a new Everbe 2.0 Ransomware variant that uses the .[].divine extension and drops a ransom note named !=How_to_decrypt_files=!.txt.
3.8.18
New Paradise Ransomware variant
![]()
Michael Gillespie found a new Paradise Ransomware variant that appends the [id-].[yourencrypter@protonmail.ch].b29extension to encrypted files.
3.8.18
WannacryV2 Ransomware
MalwareHunterTeam found a new AutoIt ransomware called wannacryV2 that appends the .wannacryv2 extension to encrypted files and provides a decryptor.
2.8.18
GandCrab Ransomware Author Bitter After Security Vendor Releases Vaccine App
![]()
The author of the GandCrab ransomware is a little bit bitter at South Korean security vendor AhnLab after the security firm released a vaccine for the GandCrab ransomware. Due to this they decided to include an alleged zero-day for the AhnLab v3 Lite antivirus in their recent builds.
2.8.18
New Scarab Ransomware variant
Michael Gillespie f found a new Scarab Ransomware variant that uses the same email from a Animus attacker. This variant appends the .anonimus.mr@yahoo.com extension to encrypted files.
28.7.18
WannaCash Ransomware discovered
Amigo-A discovered a new Russian ransomware called WannaCash that renamed files into the pattern "encrypted(file_name.file_extension)". A decrypter is available from Alex Svirid.
28.7.18
New Animus/Aurora variant
Michael Gillespie found a new variant of the Animus/Aurora ransomware that appends the .desu extension to encrypted files. It will also rename the original file name to its hex equivalent. It is still decryptable.
28.7.18
GandCrab added additional languages to payment page
Damian1338 noticed that the GandCrab team added more languages to their payment page.
28.7.18
Locky
Brad found a new ransomware calling itself Locky. This is not a new variant of the old ransomware of the same name, but an imposter. else been seeing this?
28.7.18
SamSam Ransomware Crew Made Nearly $6 Million From Ransom Payments
![]()
The SamSam ransomware has earned its creator(s) more than $5.9 million in ransom payments since late 2015, according to the most comprehensive report ever published on SamSam's activity, containing information since the ransomware's launch in late 2015 and up to attacks that have happened earlier this month.
28.7.18
BitPaymer Ransomware Infection Forces Alaskan Town to Use Typewriters for a Week
![]()
On Monday, officials from Matanuska-Susitna (Mat-Su), a borough part of the Anchorage Metropolitan Statistical Area, said they are still recovering from a ransomware infection that took place last week, on July 24.
28.7.18
Liviu Dragnea Ransomware discovered
MalwareHunterTeam found a new in-development ransomware that is based on Stupid Ransomware. This ransomware contains an image of Liviu Dragnea as its background. The sample does not currently encrypt, but if it did, it would use the .dragnea extension.
28.7.18
New Ann Ransomware
S!Ri discovered a new ransomware called Ann that renames files to the ""[AskHelp@protonmail.com]..ANN" " pattern.
28.7.18
RECOVERYOURFILES Ransomware
![]()
Michael Gillespie found a new ransomware uploaded to ID Ransomware that appends the .RECOVERYOURFILES extension and drops a ransom note named INSTRUCTIONS_RECOVER_FILES.txt.
28.7.18
New Matrix Ransomware variant
Michael Gillespie found a new variant of the Matrix Ransomware uploaded to ID Ransomware that renames files to "[BatHelp@protonmail.com].-.CORE" and drops a ransom note named #CORE_README#.rtf.
Srpen 16
New RektLocker Ransomware Discovered
A new ransomware called RektLocker was discovered by Michael Gillespie that is based on the HiddenTear source code released by Utku Sen. When installed it will encrypt files using AES encryption and then append the .rekt extension to them. It will also create a ransom note called Readme.txt that contains the bitcoin address that a payment should be sent to. Strangely, there is no method to contact the developer after payment is made. Victim's can use Michael's Hidden Tear Brute Forcer to try and get the decryption key for their files.
Srpen 16
Ransomware on Thermostats is just the Tip of the Iceberg
This past weekend at the IoT Village in the DEF CON security conference, Pen Test Partners set to out to demonstrate the sad state of security when it comes to IoT devices. They did this buy showing how they could easily hack a smart thermostat so that ransomware could be installed on it.
Srpen 16
With the looming threat of Ransomware, should companies stockpile Bitcoins?
![]()
With the threat of ransomware hanging over every company's head, does it make sense for companies to stockpile a few bitcoins in the event of a ransomware attack? Getting bitcoins is not the easiest of tasks and with the a ransomware timer counting down, does it make sense to have some on hand?
Srpen 16
Smrss32 Ransomware that pretends to be CryptoWall Discovered
A ransomware that has been out for a while, but only yesterday was a sample provided by a victim on the forums. This ransomware creates an incredibly lengthy ransom note that states it is CryptoWall and then tells you to pay 1 bitcoin to a specified bitcoin address. You are then prompted to email helprecover@mail.ru after payment to get a decryption key. Encrypted files will have the .encrypted extension appended to them and then ransom note is named _HOW_TO_Decrypt.bmp. This ransomware appears to be installed manually via Remote Desktop and as part of a kit of multiple files. It may be possible to decrypt this ransomware, so if you have been affected by this, please do not pay the ransom.
Srpen 16
BloodDolly Releases a Decryptor for the PizzaCrypt/Juicylemon Ransomwares
![]()
BloodDolly has released a decryptor for the PizzaCrypt and Juicylemon ransomware infections. For those who are infected with it, you can download the decryptor from the following URL: http://download.bleepingcomputer.com/BloodDolly/JuicyLemonDecoder.zip This decryptor will decrypt files that have the following extensions:
.id-{number}_
.id-{number}_sos@juicylemon.biz
.id-{number}_*@juicylemon.biz*protonmail.com*
.id-{number}_*@juicylemon.biz_BitMessage_*
.id-{number}_maestro@pizzacrypts.info
Support for this ransomware can be found in this topic.
Srpen 16
PokemonGo Ransomware installs Backdoor Account and Spreads to other Drives
Michael Gillespie discovered a new ransomware that pretends to be PokemonGo. This ransomware is currently in development as it uses a Command & Control server on a private IP address and has a static AES encryption password. When it encrypts files it will append the .locked extension to encrypted files. It will also create a Arabic ransom note on the Desktop called هام جدا.txt.
Mosh has posted further analysis of this ransomware in Spanish.
The icon used by the program is of Pikachu:
Srpen 16
Development version of the Hitler-Ransomware Discovered
It looks like file deletion is becoming a standard tactic in new ransomware applications created by less skilled ransomware developers. This is shown in a new ransomware called Hitler-Ransomware, or mispelled in the lock screen as Hitler-Ransonware, that has been discovered by AVG malware analyst Jakub Kroustek. This ransomware shows a lock screen displaying Hitler and then states that your files were encrypted. It then prompts you enter a cash code for a 25 Euro Vodafone Card as a ransom payment to decrypt your files. In the current version this ransomware does encrypt your files, but rather just removes the extension. On reboot, it deletes all of the files under the %UserProfile% folder.
Červenec 16
Side-by-side comparisons of the CrypMIC and CryptXXX Ransomware Infections
TrendMicro has discovered that there is a new family of ransomware called CrypMIC that appears very similar to the CryptXXX ransom family. At this time it is unknown if this is just a new ransomware trying to benefit from CryptXXX success or if its a split in the CryptXXX development tree. This article shows side-by-side differences between the two ransomware families.
Červenec 16
New Simple_Encoder Ransomware Discovered
The Simple_Encoder, or Tilde Ransomware, is a ransomware discovered by Michael Gillespie that will encrypt your data using AES encryption and then adds a tilde, or .~ extension, to encrypted files. For each folder that a file is encrypted, it will create a _RECOVER_INSTRUCTIONS.ini ransom note, which is shown below. If you are affected by this ransomware, please post in the Simple_Encoder Ransomware Help & Support Topic as we may be able to help.
Červenec 16
The NoMoreRansom Project goes Public
![]()
A new project called NoMoreRansom was created by the National High Tech Crime Unit of the Netherlands’ police, Europol’s European Cybercrime Centre, Kaspersky Lab, and Intel Security was developed and announced to help victims of ransomware. This site contains info about ransomware, some decryptors, and a way of identifying what ransomware has infected you.
Červenec 16
Chimera Ransomware Decryption Keys Released by Petya Devs
The devs behind the Mischa and Petya ransomware have leaked approximately 3500 RSA decryption keys for the Chimera Ransomware. These keys are in hex format, but can be converted back to their normal format and used within a decryptor by a security company or professional.
Červenec 16
Petya and Mischa Ransomware Affiliate System Publicly Released
Today, the Petya and Mischa Ransomware devs have made their Ransomware as a Service, or RaaS, open to the public. For the past few months, the Petya & Mischa RaaS has been been in testing with a limited amount of supposed high volume distributors. As of today, any would-be criminal can signup and become an official distributor. Unfortunately, this will most likely lead to a greater amount of distribution campaigns for this ransomware.
Červenec 16
New Jager Ransomware Discovered
A new ransomware was discovered by AVG malware analyst Jakub Kroustek called Jager Ransomware. The command & control server for the ransomware was disabled fairly quickly, so it does not appear that this ransomware very widespread.
Červenec 16
Turkish Ransomware called Uyari Discovered
This was posted a while back, but hadn't heard about it so adding it to this weeks article. The Uyari Ransomware is a ransomware discovered by Michael Gillespie whose ransom notes are written in Turkish and demands 2 bitcoins as a ransom. When encrypting files it will append the .locked extension to encrypted files and create a ransom note called DOSYALARINIZA ULAŞMAK İÇİN AÇINIZ.html on the desktop. Further analysis of this ransomware was done by Mosh. This ransomware can be decrypted and any victim's should ask for help in the Uyari Ransomware Help & Support Topic.
Červenec 16
We Are Anonymous Jigsaw Ransomware Variant Discovered
A new variant of the Jigsaw Ransomware has been discovered by Michael Gillespie that uses a new Anonymous themed background for the ransom note. Though there has been a previous variant of Jigsaw that included a Guy Fawkes mask, this new one implies that Anonymous is involved with the ransomware. The ransom screen's background now states "We are Anonymous. We Are Legion. We do not forget. We do not forgive. Expect us.". The good news is that Jigsaw continues to be easily decrypted and Michael's Jigsaw Decryptor has been updated to decrypt this variant.
Červenec 16
Kaspersky rakhnidecryptor.exe to decrypt the Chimera Ransomware
![]()
Kaspersky has updated their RakhniDecryptor tool to include support for decrypting the Chimera Ransomware. This tool only supports the 3,500 keys that were leaked by the Petya Devs.
Prosinec 16
PadCrypt 3.1.2 Released
MalwareHunterTeam discovered that PadCrypt has been upgraded to version 3.1.2. No significant changes were made.
Prosinec 16
Ransomware Author "Pornopoker" Arrested in Russia
![]()
Russian authorities have arrested a man suspected of writing and distributing ransomware. The suspect, whose name hasn't been released yet, goes by the nickname of Pornopoker.
Prosinec 16
Emsisoft released a decryptor for the latest Nemucod variant
![]()
Fabian Wosar of Emsisoft has released a decryptor for the latest Nemucod campaign that is underway. The decryptor can be downloaded from here.
Prosinec 16
New version of the Apocalypse Ransomware Released
![]()
Emsisoft security researcher xXToffeeXx discovered a new version of the Apocalypse Ransomware that uses ransom note named [md5].txt and files will be encrypted as [filename].ID-*8characters+countrycode[cryptservice@inbox.ru].[random7characters]
Prosinec 16
New Globe ransomware released that uses the .lovewindows extension
![]()
Security researcher Michael Gillespie discovered a new variant of the Globe Ransomware that apppends the .lovewindows extension to encrypted files. It also uses the email address bahij2@india.com as a point of contact.
Prosinec 16
Kelihos Botnet Delivering Shade (Troldesh) Ransomware with No_More_Ransom Extension
Over the last two weeks, the Kelihos spam botnet has been busy spreading the latest version of the Shade ransomware (also known as Troldesh), which now appends the ".no_more_ransom" extension at the end of each encrypted file. Their gesture is a sign of irony, as the NoMoreRansom project has released a free decrypter over the summer that can help victims unlock files encrypted by this threat.
Prosinec 16
New screenlocker with File Encryption Discovered
GData malware analyst Karsten Hahn has discovered a new screen locker that also encrypts files. Appears to be buggy as it does not appear to encrypt anything, but does contain an decryption routine. It is supposed to encrypt files and append the .encrypted extension to encrypted files.
Prosinec 16
Locky Ransomware switches to Egyptian Mythology with the Osiris Extension
Once again, the developers of the Locky Ransomware have decided to change the extension of encrypted files. This time, the ransomware developers moved away from Norse gods and into Egyptian mythology by using the .osiris extension for encrypted files.
Prosinec 16
Petya Ransomware Returns with GoldenEye Version, Continuing James Bond Theme
The author of the Petya-Mischa ransomware combo has returned with a new version that uses the name GoldenEye Ransomware, continuing the malware's James Bond theme. Malwarebytes' researcher hasherezade has also posted some analysis.
Prosinec 16
New Scheme: Spread Popcorn Time Ransomware, get chance of free Decryption Key
Yesterday a new in-development ransomware was discovered by MalwareHunterTeam called Popcorn Time that intends to give victim's a very unusual, and criminal, way of getting a free decryption key for their files. With Popcorn Time, not only can a victim pay a ransom to get their files back, but they can also try to infect two other people and have them pay the ransom in order to get a free key.
Prosinec 16
New HACKED Jigsaw Ransomware Variant Discovered
Security researcher Michael Gillespie discovered a new Jigsaw Ransomware variant called HACKED. You can use Michael's Jigsaw Decryptor to get decrypt your files for free.
Prosinec 16
New SamSam Ransomware variant Discovered
Security researcher Michael Gillespie discovered a new variant of the SamSam Ransomware. This variant uses the .VforVendetta extension for encrypted files and a ransom note called 000-PLEASE-READ-WE-HELP.html.
Prosinec 16
Modified EDA2/Hidden-Tear Ransomware For Sale
Security researcher Jiri Kropac discovered a modified version of the EDA2/HiddenTear Ransomware for sale on underground criminal sites.
Prosinec 16
"Proof of Concept" CryptoWire Ransomware Spawns Lomix and UltraLocker Families
A new open-source ransomware project called CryptoWire was uploaded on GitHub as a "proof of concept," has now spawned three new ransomware families that are infecting users in real-life.
Prosinec 16
New CryptoWire-based UltraLocker Discovered
GData malware analyst Karsten Hahn discovered a new variant of the open-source AutoIT ransomware CryptoWire ransomware was discovered called UltraLocker.
Prosinec 16
CyberSplitter Ransomware 2.0 Released
GData malware analyst Karsten Hahn discovered version 2.0 of the CyberSplitter ransomware. This ransomware is based off of the Hidden-Tear open source ransomware.
Prosinec 16
New Locked-In Ransomware Discovered
GData malware analyst Karsten Hahn is on fire with the discovery of the new Locked-In ransomware. This ransomware will encrypt your files and create ransom notes called RESTORE_CORUPTED_FILES.HTML. Personally I think the devs screwed up when they made this ransomware as it prob should have been called Locked-Out.












_small.jpg)